
1
Report to Congress on Best Practices
Regarding Enforcement of Anti-Stalking Laws
Reporting Requirement
Section 3 of the Combat Online Predators Act (PL No. 116-249) requires the Attorney General to
submit a report to Congress on best practices regarding enforcement of anti-stalking laws, one
year after the date of enactment of the Act. The report is to include an evaluation of federal,
tribal, state, and local efforts to enforce laws relating to stalking;” and “identify and describe
those elements of such efforts that constitute the best practices for the enforcement of such
laws.”
Background
Roughly 1 in 3 women, and 1 in 6 men in the United States have suffered some form of stalking
in the course of their lifetime.
1
Stalking is challenging to police effectively as it is a pattern-based, rather than an incident-
based, crime. Responding to stalking cases often necessitates specialized knowledge and a
significant investigative effort.
2
Research supported by the Department of Justice (DOJ), Office
on Violence Against Women (OVW) suggests that the law enforcement response would be
improved with the implementation of assessment tools for identifying stalking behaviors within
the context of other intimate partner violence (IPV)-based crimes, as well as by providing
specific training for officers.
3
A detailed summary of research, statistics, best practices, and OVW grantees’ efforts related to
stalking can be found in OVW’s reports to Congress pursuant to 34 U.S.C. § 12049, which
requires a report every even-numbered fiscal year to include information about the incidence
of stalking and domestic violence and evaluating the effectiveness of anti-stalking efforts and
legislation. OVW’s reports to Congress are available here:
https://www.justice.gov/ovw/reports-congress.
1
Smith, S. G., Basile, K. C., & Kresnow, M. (2022). The National Intimate Partner and Sexual Violence Survey (NISVS): 2016/2017
Report on Stalking. National Center for Injury Prevention and Control, Centers for Disease Control and Prevention.
https://www.cdc.gov/violenceprevention/pdf/nisvs/nisvsstalkingreport.pdf
2
National Institutes of Justice. (2022, February 1). Current State of Knowledge about Stalking and Gender-Based Violence: The
Known, Unknown, and Yet To Be Known [Webinar].
https://nij.ojp.gov/events/current-state-knowledge-about-stalking-and-gender-based-violence-known-unknown-and-yet-be.
3
Garza, A.D., Franklin, C. A., & Goodson, A. (2020). The nexus between intimate partner violence and stalking: Examining the
arrest decision. Criminal Justice and Behavior, 47(8), 1014-1031, available at:
https://journals.sagepub.com/doi/pdf/10.1177/0093854820931149.

2
Stalking Victimization in the United States
This section contains updated information to reflect federal data on stalking published in 2022
by the DOJ’s Bureau of Justice Statistics and the Centers for Disease Control and Prevention in a
recent report to Congress submitted pursuant to 34 U.S.C. § 12049. (BJS 2019 and 2022 reports;
CDC NISVS 2022 report)
The Bureau of Justice Statistics (BJS) reports that approximately 3.4 million people age 16 or
older were stalked in 2019,
4
and the National Intimate Partner and Sexual Violence Survey
(NISVS), administered by the Centers for Disease Control and Prevention (CDC), has found that
about 1 in 3 women and 1 in 6 men have experienced stalking at some point in their lives.
5
Women who are divorced or separated face the highest rate of stalking.
6
The majority of
victims are stalked by people they know, and 43.4% of female victims and 32.4% of male
victims of stalking are stalked by a current or former intimate partner.
7
Stalking victims report that stalking tactics most often include the perpetrator: following the
victim, approaching the victim or showing up in places, such as the victim’s home, work, or
school; using GPS technology or equipment to monitor or track the victim’s location; leaving
strange or potentially threatening items for the victim to find; sneaking into the victim’s home
or car and doing things to scare the victim by letting the victim know they had been there; using
technology such as a hidden camera, recorder, or computer software to spy on the victim from
a distance; making unwanted phone calls to the victim; sending the victim unwanted emails,
text or photo messages, or social media messages; and sending the victim cards, letters,
flowers, or presents when they knew the victim does not want.
8
Perpetrators who stalk victims do so repeatedly, and over a significant period of time: Twenty-
four percent of stalking victims said the stalking behavior lasted for two years or more, and
10.8% said it happened too many times to count.
9
In addition to the relentless nature of the crime, stalking is also a significant risk factor for
domestic violence-related homicide. In a study of cases of actual or attempted domestic
violence homicide involving a female victim who was physically assaulted by her violent partner
in the preceding year, nearly all (90%) of the victims were also stalked by their assailant.
10
Of
the women in that study who were murdered, 54% had reported the stalking to police before
they were killed. Another study assessing police records found that domestic violence cases
4
Morgan, R. E., & Truman, J. L. (2022). Stalking Victimization, 2019. U.S. Department of Justice Bureau of Justice Statistics.
Available at: https://bjs.ojp.gov/content/pub/pdf/sv19.pdf.
5
Smith, Basile, & Kresnow (2022).
6
Morgan & Truman (2022).
7
Smith, Basile, & Kresnow (2022).
8
Smith, Basile, & Kresnow (2022).
9
Morgan & Truman (2022).
10
McFarlane, J., Campbell, J.C., Wilt, S., Sachs, C., Ulrich, Y., and Xu, X. (1999). Stalking and intimate partner femicide. Homicide
Studies, 3(4), 300–316.

3
with features of stalking or stalking charges were more threatening and violent than cases
without elements of stalking.
11
Young adults and people in the lowest income brackets experience higher rates of stalking:
people in households with incomes under $10,000 were more likely to be stalking victims than
people with household incomes over $10,000.
12
More than half of female stalking victims report that they were first stalked before age 25, and
about 1 in 4 were first stalked before age 18; those figures are similar for male victims of
stalking.
13
Research has found that stalking may be more common on college campuses than in
the general population.
14
According to one study of nearly 1,600 college students, 42.5% had
experienced some form of stalking victimization. However, victims may not recognize stalking
as a crime.
15
Of those students reporting behavior that qualified as stalking, only about one
quarter (24.7%) self-identified as stalking victims, and their likelihood of acknowledging the
behavior as stalking was linked with more severe and injurious actions by the offenders.
16
Being stalked, and suffering the fear and threats that characterize the crime, is significantly
correlated with the severity of symptoms of posttraumatic stress disorder (PTSD) and
psychological distress endured by female victims.
17
Stalking burdens victims with numerous
tangible and intangible costs, from emotional trauma to financial ruin. Anxiety, insomnia, and
depression, and other symptoms of traumatic stress are much higher among stalking victims
than people who have not been stalked.
18
Furthermore, stalking by a current or former
intimate partner has been found to escalate victims’ fear and distress, with victims being
significantly afraid that their stalkers would physically or sexually assault them, harass them and
their loved ones, threaten their children, cause financial problems, or humiliate them publicly.
19
In addition to the emotional and psychological toll of stalking, victims also face financial
hardship as they may have to move, cancel cell phone plans, change jobs, reduce employment,
or purchase expensive security systems in attempts to remain safe. One study found that
domestic violence victims who were stalked after obtaining a protection order incurred an
11
Klein, A. K., Salomon, A., Huntington, N., Dubois, J., & Lang, D. (2009). A statewide study of stalking and its criminal justice
response. (NCJ 228354). Washington, DC: U.S. Department of Justice, National Institute of Justice.
12
Morgan & Truman (2022).
13
Smith, Basile, & Kresnow (2022).
14
See, for example: Buhi, E. R., Clayton, H., & Surrency, H. (2009). Stalking victimization among college women and subsequent
help-seeking behaviors. Journal of American College Health, 57(4), 419–426.
15
McNamara, C. L., & Marsil, D. F. (2012). The prevalence of stalking among college students: The disparity between
researcher-and self-identified victimization. Journal of American College Health, 60(2), 168–174.
16
McNamara, C. L., & Marsil, D. F. (2012).
17
Fleming, K. N., Newton, T. L., Fernandez-Botran, R., Miller, J. J., & Burns, V. E. (2012). Intimate partner stalking victimization
and posttraumatic stress symptoms in post-abuse women. Violence Against Women, 18(12), 1368-1389.
18
Blaauw, E., Winkel, F. W., Arensman, E., Sheridan, L., & Freeve, A. (2002). The toll of stalking: The relationship between
features of stalking and psychopathology of victims. Journal of Interpersonal Violence, 17(1), 50-63; and, Brewster, M. (2002).
Trauma symptoms of former intimate stalking victims. Women and Criminal Justice, 13(2/3), 141-161.
19
Logan, T. K., Walker, R., Hoyt, W., & Faragher, T. (2009). The Kentucky civil protective order study: A rural and urban multiple
perspective study of protective order violation consequences, responses, and costs. (NCJ 228 350). Washington, D.C.: U.S.
Department of Justice, National Institute of Justice. Available at: http://www.ncjrs.gov/pdffiles1/nij/grants/228350.pdf.

4
average of $610 in property damage or loss in a six-month period, compared to $135 for victims
whose abusers violated protection orders in ways that did not include stalking, and $15 for
those whose protection orders were not violated and who were not stalked.
20
Victims who
were stalked after the protection order was issued also lost more work time (78 hours) than
victims who did not experience further abuse or stalking while a protection order was in place
(4 hours).
21
Stalking is an underreported crime: around 30% of stalking victims in 2019 reported it to
police.
22
Victims’ reasons for not reporting include: a belief that the police cannot or will not do
anything, fear that they will not be believed, being afraid of the perpetrator, not wanting law
enforcement or courts involved in the matter, thinking that the perpetrator’s actions are not
serious enough to warrant reporting to police, and not having proof of stalking.
23
Furthermore,
research has documented that stalking is rarely identified in domestic violence cases that
include elements of stalking,
24
and people arrested for stalking often are not prosecuted.
25
OVW-Supported Training and Technical Assistance to Enforce Laws Related to Stalking and
Best Practices
To ensure the field has appropriate training, technical assistance, and access to best practice
information when addressing stalking, OVW has funded the Stalking Prevention Awareness and
Resource Center (SPARC). SPARC maintains a thorough and informative website with resources
for victim services providers, law enforcement officers, prosecutors, and corrections personnel.
SPARC identifies and derives its materials from best practices in each of these professions and
packages them in useful, engaging formats for the intended audience. The full spectrum of best
practices, tools, briefs, and more can be found at https://www.stalkingawareness.org/. Below is
a sampling of these resources organized by profession.
For victim services providers:
• SPARC provides these Quick Tips for stalking response strategies;
• A Guide for Advocates on responding to stalking, which is also available in Spanish; and
20
Logan, T. K., & Walker, R. (2010). Toward a deeper understanding of the harms caused by partner stalking. Violence and
Victims, 25(4), 440-455.
21
Logan & Walker (2010).
22
Morgan & Truman (2022).
23
Logan, T. K., Cole, J., Shannon, L., & Walker, R. (2006). Partner stalking: How women respond, cope, and survive. New York:
Springer Publishing Company; Tjaden, P. & Thoennes, N. (1998). Stalking in America: Findings from the national violence against
women survey. (NCJ 169 592). Washington, DC/Atlanta, GA: National Institute of Justice and the Centers for Disease Control
and Prevention; and Logan, T. K., Walker, R., Hoyt, W., & Faragher, T. (2009).
24
See, for example: Tjaden, P. & Thoennes, N. (2001). Stalking: Its role in serious domestic violence cases. Washington DC: U.S.
Department of Justice, National Institute of Justice; and Caperona, B. (2007). Domestic Violence in New Mexico, 2006 Highlights.
Albuquerque, NM: State of New Mexico, Department of Health, Office of Injury Prevention.
25
Klein, A. K., Salomon, A., Huntington, N., Dubois, J., & Lang, D. (2009).

5
• Addressing Stalking: A Checklist for Domestic and Sexual Violence Organizations, which
is also available in Spanish.
For law enforcement officers:
• SPARC provides this brief, informative tip sheet on recognizing stalking behaviors;
• This incident log provides a tool to assist officers in examining a pattern of stalking
behaviors; and
• The SPARC website links to the Stalking and Harassment Assessment and Risk Profile
(SHARP), a tool developed at the University of Kentucky that allows officers or victims to
enter key pieces of data about the stalking behavior and returns an assessment of risk
based on an empirically validated 14-factor model and a clear, concise narrative of the
case.
For prosecutors:
• SPARC publishes the Prosecutor’s Guide to Stalking, a guidebook for understanding the
crime of stalking, working with victims, presenting evidence, and more;
• SPARC directs prosecutors to webinars presented by SPARC’s parent organization,
Aequitas: The Prosecutor’s Resource on Violence Against Women. One such webinar is:
#GUILTY: Identifying, Preserving, and Presenting Digital Evidence; and
• SPARC presents custom training by request on a range of topics aimed at increasing the
rate of successful prosecution for stalking.
For corrections and probation personnel:
• SPARC publishes Responding to Stalking: A Guide for Community Corrections Officers to
educate officers on proper supervision of individuals convicted of stalking; and
• This checklist by SPARC as well as the SHARP tool can be used by corrections
professionals to document, assess, and understand stalking behaviors, whether in a
penal institution or by supervisees.
For college/university campus professionals:
• SPARC offers Quick Tips, a fact sheet, and an infographic tailored to campus
populations;
• Talking Stalking: Tips for Prevention/Awareness Educators;

6
• Tips for public awareness campaigns in campus communities; and
• Tips for campus stalking investigations and hearings.
For judicial officers:
• SPARC provides a Judicial Officers Bench Card on stalking; and
• A Judicial Officer’s Guide to stalking.
The materials listed above are compiled in this report, and additional resources and training
opportunities for professionals can be found at: https://www.stalkingawareness.org/.

STALKING RESPONSE STRATEGIES
FOR VICTIM SERVICE PROVIDERS
This project was supported by Grant No. 2017-TA-AX-K074 awarded by the Office on Violence Against Women, U.S. Department of Justice. The opinions,
findings, conclusions, and recommendations expressed in this publication/program/exhibition are those of the author(s) and do not necessarily reflect the
views of the Department of Justice, Office on Violence Against Women.
1000 Vermont Avenue NW, Suite 1010 | Washington, DC 20005 | (202) 558-0040 | stalkingawareness.org
@FollowUsLegally
DID YOU KNOW
Stalking is a dangerous crime that affects an estimated 13.5 million women and men each
year. Stalking — generally defined as a pattern of behavior directed at a specific person
that would cause a reasonable person to feel fear for their safety or the safety of others,
and/or suffer substantial emotional distress — is a crime under the laws of all 50 states,
the District of Columbia, the U.S. territories, and the federal government. Stalking can
have devastating and long-lasting physical, emotional, and psychological effects on
victims. The prevalence of anxiety, insomnia, social dysfunction, and severe depression is
much higher among stalking victims than in the general population. Victim advocates can
help victims devise a safety plan, navigate the criminal justice system, assert their rights
as crime victims, and obtain the services and support they need and to which they are
entitled.
HOW VICTIM ADVOCATES CAN HELP
1. Recognize that stalking is a pattern of behavior, and a stalking victim’s level of fear
and need for resources and assistance may vary and change based on the stalker’s
behaviors.
2. Realize that stalking victims may maintain contact with their offenders to keep
themselves (or loved ones) safe. Work with victims to establish safety plans.
3. Documentation can be extremely helpful in stalking cases. Victims could consider
using a documentation log.
4. Collaborate with others in your community, such as law enforcement, prosecutors,
and community corrections, to help protect victims of stalking. Health care providers
and members of faith communities also can be vital resources.
5. Work with law enforcement, prosecutors, and others to educate victims about the
ongoing dynamics of stalking cases and what evidence and documentation may be
required if they choose to report to the police.
While legal
definitions of
stalking vary from
one jurisdiction to
another, a good
working definition
of stalking is:
a pattern of
behavior directed at
a specific person
that would cause a
reasonable person
to feel fear for their
safety or the safety
of others, and/or
suffer substantial
emotional distress.

RESPONDING
TO STALKING
A GUIDE FOR ADVOCATES
This project was supported by Grant No. 2017-TA-AX-K074 awarded by the U.S. Department of Justice, Oce on Violence Against Women (OVW).
The opinions, ndings, conclusions, and recommendations expressed in this program are those of the authors and do not necessarily reect the views of OVW.

RESPONDING TO STALKING: A GUIDE FOR VICTIM ADVOCATES
TABLE OF CONTENTS
UNDERSTANDING STALKING
About the Crime of Stalking 4
The Intersection of Stalking with Other Crimes 7
The Impact of Stalking on Victims 9
THE ADVOCATE’S ROLE IN ASSISTING STALKING VICTIMS
Common Victim Reactions and Responses 12
Safety Planning 12
Protection Orders/Restraining Orders 16
Address Confidentiality Programs 17
Crime Victim Compensation 17
SCENARIOS
Case Scenarios 19-20
Conclusion 21

RESPONDING TO STALKING: A GUIDE FOR VICTIM ADVOCATES 3
UNDERSTANDING
STALKING

RESPONDING TO STALKING: A GUIDE FOR VICTIM ADVOCATES 4
ABOUT THE CRIME OF STALKING
INTRODUCTION
Stalking is a crime under the laws of all 50 states, the
District of Columbia, the U.S. Territories, Federal law,
and many tribal codes. An estimated 7.5 million
people in the United States are stalked every year;
yet the crime is seldom charged or prosecuted.
1
Stalking diers from
most crimes in two
important ways:
it involves repeat
victimization—it
is not a single
incident—and it is
defined in part by
the impact and toll it has on the victim. In fact, many
of the individual acts that make up stalking may be
legal by themselves and appear harmless to someone
unfamiliar with the case.
To complicate matters further, no single legal
definition exists: stalking varies widely in statute
definition, scope, crime classification, and associated
penalties.
How, then, can you support victims of the crime? To
recognize stalking and best help victims, advocates
and other professionals must be able to identify
stalking behaviors and help victims navigate the
criminal and civil justice systems, if victims are
choosing to access those systems for support.
DEFINING STALKING
In general, a good working denition of stalking is:
a course of conduct directed at a specic person
that would cause a reasonable person to feel fear.
Important components of this denition include:
• Course of conduct – a pattern of behavior involving
more than one action, committed over a period of
time (however short), that demonstrates a consistent
objective.
• Reasonable person – a legal standard of objectivity
used in place of subjective perceptions. It asks,
would another person in similar circumstances be
afraid because of the perpetrator’s behavior?
• Level of Fear – how fearful the stalking behaviors
make the victim. Criminal laws vary widely on what
level of fear a victim must experience to make the
stalker’s behavior criminal. Your state’s law may
require the victim to:
• Fear for their safety or experience substantial
emotional distress;
• Feel terrorized, frightened, intimidated, or
threatened, or fear that the perpetrator intends
to injure them or another person or damage
their property or another person’s property;
• Fear serious bodily injury or death.
1
Katrina Baum et al., “Stalking Victimization in the United States,”
(Washington, DC: Bureau of Justice Statistics, 2009).
INDIVIDUAL ACTS
THAT MAKE UP
STALKING MAY BE
LEGAL AND
APPEAR HARMLESS.
Kim has been dating Tyson for 2 years. He calls her at work every day when she is eating lunch to see how
her day is going and prefers her to come straight home after work so they can spend time together. In the last
3 months, he has started getting upset if she doesn’t answer when he calls. Twice in the last week he drove to
the office to find out where she was. When she runs errands, he texts her multiple times each hour, wanting
to know exactly where she is. Kim didn’t mind at first, but it started to get worse after Tyson lost his job. He
started calling more frequently, leaving notes on her car while she was at work, and emailing her coworkers.
Kim has started leaving work a little early to make sure she is home when he says she should be. She tells you
she is afraid. He’s never physically hurt her, but his behavior is getting more unpredictable.
The course of conduct in this example is demonstrated by the perpetrator's repeated calls, visits to her office,
and insistence on knowing her location. Kim is shown to be a reasonable person because most people in her
circumstance would also experience fear. You are able to identify her level of fear because she tells you she is
afraid because he is unpredictable. She has also altered her behavior because she is afraid of what might
happen if she is late.

RESPONDING TO STALKING: A GUIDE FOR VICTIM ADVOCATES 5
UNDERSTANDING CONTEXT
AND FEAR
Compared to most other crimes, stalking is unique in
that the context of the stalking behavior is critical to
identifying and understanding what is occurring. The
victim plays a critical role in defining whether their
experience can be classified as stalking because the
perpetrator’s behaviors can only be identified as
stalking when the impact of those behaviors on the
victim is considered. Understanding a victim’s
response and level of fear may be difficult without
knowing the full context of the course of conduct and
any relationship that may exist between the victim and
the offender.
In some cases, the victim may not explicitly express
or display fear. The victim may be afraid or unwilling
to name the emotion, may believe that showing fear
will escalate the situation or provide satisfaction to
the stalker, or may wish to minimize the danger. Some
victims may struggle to admit feeling fearful as a
result of social norms regarding masculinity and
bravery. Advocates should provide access to the same
levels of support for all victims regardless of how
fearful they appear.
Often, perpetrators of stalking exploit a victim’s
specific fears or phobias and communicate
threats covertly in ways that seem harmless to
outsiders. For instance, perpetrators may send
the victim unwanted messages or gifts that
seem innocuous or even romantic—such as a
bouquet of roses. But the victim recalls the
perpetrator threatening that the day they
received roses would be the day they were
killed. Without this context, the victim’s terror
may seem irrational to a responder. Indeed,
perpetrators may provoke this reaction in part
to discredit the victim or cast doubt on the
victim’s mental health.
WORKING WITH UNDERSERVED
POPULATIONS
Victims of underserved populations often face
additional and unique barriers to the obstacles they
already face as stalking victims. Included in this
population of victims are children, people with
disabilities, older adults, lesbian, gay, bisexual,
transgender, and queer/questioning (LGBTQ)
identified individuals, American Indians and Alaska
Natives, victims with limited English proficiency,
immigrants, formerly incarcerated individuals, people
of color, individuals who are undocumented, and
others from historically marginalized communities. As
an advocate, it is essential that you consider the
context and the potential barriers a victim may face
when reporting the crime, seeking services, and
staying safe. These barriers may include language,
fear of law enforcement, accessibility, and care needs.
It is important to consider this for every victim,
because many disabilities or cultural needs may not be
readily apparent. While each situation may or may not
occur, you have the ability to enhance the safety of
victims by helping them prepare for any possible
situation. The best way to determine potential barriers
to safety is to ask victims if they would like to share
any concerns. Doing so will assist in safety planning
as well as the search for services.
ADVOCATES SHOULD
PROVIDE ACCESS TO THE
SAME LEVELS OF SUPPORT
FOR ALL VICTIMS REGARDLESS OF
HOW FEARFUL THEY APPEAR.

RESPONDING TO STALKING: A GUIDE FOR VICTIM ADVOCATES 6
STALKING BEHAVIORS
Perpetrators of stalking engage in many different
behaviors, and most use multiple tactics.
2
They
frequently invest time, energy, and money in
monitoring and pursuing their victims. Although
many stalking behaviors are not criminal as a single
occurrence, when viewed as a course of conduct that
causes the victim fear or distress, they add up to
stalking.
Common stalking behaviors include:
• Repeated phone calls, voicemails, emails, or text
messages
• Monitoring a victim’s phone activity or computer
use
• Sending unwanted gifts, letters, or cards
• Posting information or spreading rumors about the
victim on social media sites, in public places, or by
word of mouth
• Searching for information about the victim by
conducting public records or online searches, hiring
private investigators, digging through the victim’s
garbage, or contacting the victim’s friends, family,
neighbors, or co-workers
• Using technology, such as hidden cameras, to watch
the victim
• Driving by, waiting at, or showing up at the victim’s
home, school, or work
• Following the victim, either in person or via the use
of technology (e.g., GPS or location-based apps)
• Using a third party to contact or stalk the victim (i.e.,
proxy stalking)
• Committing identity theft or financial fraud against
the victim, such as opening, closing, or taking money
from accounts
• Using children to harass or monitor the victim
• Vandalizing or destroying a victim’s property, car, or
home
• Violating protective orders or other injunctions
• Threatening to hurt the victim or their family,
friends, or pets
• Threatening to kill the victim or others, self, or pets
These behaviors are not exhaustive and may change
or escalate over time. The average duration of stalking
is approximately two years, although intimate partner
stalking tends to last longer than non-intimate partner
stalking.
3
Advocates should check in regularly with
victims about the perpetrator’s stalking behaviors
as perpetrators of stalking often modify their tactics
based on the victim’s response. Also note that victims
commonly experience times of little stalking activity
and times of constant activity; a victim’s level of
engagement with the system may fluctuate
correspondingly.
STALKING THROUGH THE USE OF
TECHNOLOGY
Stalkers frequently use technologies, often legal
technologies, to stalk, monitor, and track their victims.
Comprehensive, up-to-date resources for advocates and
victims on how to best safety plan for stalking via
technology, can be found at the Safety Net team’s
website. Please see https://www.techsafety.org/ for more
information.
THREAT ASSESSMENT
Threat assessment is a process used to determine the
level of danger posed by a perpetrator to a victim at a
particular point in time. It is important to keep these
factors in mind when working with a victim. The most
dangerous perpetrators are those who:
• Engage in actual pursuit of the victim
• Possess or are interested in weapons
• Commit other crimes such as vandalism or arson
• Are prone to emotional outbursts and rage
• Have a history of violating protection orders,
substance abuse, mental illness and/or violence,
especially toward the victim
• Have made threats of murder or murder-suicide
The most dangerous times for a stalking victim are when:
• The victim has separated from the stalker
• The stalker has been arrested or served with a
protection order
• The stalker has a major negative life event, such as
the loss of a job or being evicted
• The stalking behaviors increase in frequency or
escalate in severity
2
Kris Mohandie et al., “The RECON Typology of Stalking: Reliability and
Validi- ty Based Upon a Large Sample of American Stalkers,” Journal of
Forensic Science 51, No. 1(2006).
3
P. Tjaden and N. Thoennes. “Stalking in America: Findings from the National
Violence Against Women Survey,” Research Report, Washington, DC: U.S.
De- partment of Justice, National Institute of Justice and Centers for Disease
Control and Prevention, 1998.

RESPONDING TO STALKING: A GUIDE FOR VICTIM ADVOCATES 7
THE INTERSECTION OF STALKING WITH
OTHER CRIMES
Stalking frequently co-occurs with other types of
victimization and criminal behavior. The stalking
course of conduct may include individually illegal acts
such as trespassing or property damage. Stalking
behavior may also be a precursor to other crimes, such
as sexual assault or homicide. Making the connection
between stalking and other associated crimes benefits
both the victim and the criminal justice system as a
whole. When criminal justice system personnel can
identify other crimes committed by the stalker, they
can more effectively establish the course of conduct
against the victim, take reports, gather critical
evidence, and file charges.
Some of the crimes that can intersect with stalking are
as follows:
INTIMATE PARTNER VIOLENCE
One study found that 81 percent of victims who were
stalked by a current or former intimate partner had
been physically assaulted by that partner.
4
A common
misconception is that stalking usually begins when a
victim of intimate partner violence leaves the
relationship. In fact, 57 percent of intimate partner
stalking victims report that the stalking behaviors
began before the relationship ended.
5
Checking the
victim’s phone logs, reading the victim’s emails,
confirming the victim’s whereabouts—these behaviors
may seem normal to the victim or less alarming than
any physical abuse. However, identifying these
behaviors as stalking is critical. Research is clear: when
physical abuse and stalking co-occur, the victim is at
greater risk of violence — including homicide
— and will need a comprehensive safety plan.
Perpetrators of intimate partner stalking are more
likely to physically approach the victim at their home
or place of work. They are also more likely to use a
third party, such as a family member or friend, to
further their stalking (for instance, asking a third party
to provide personal information about the victim, keep
track of where the victim is going, or communicate
messages to the victim). The combined elements of
stalking and physical violence require thoughtful and
detailed attention to additional risks.
HOMICIDE
Another study found that nearly 70 percent of
femicide victims were physically assaulted before
their murder. Of those, 90 percent had also
experienced at least one episode of stalking in the 12
months prior to their murder.
6
Perpetrators of
intimate partner stalking are better able to exploit the
victim’s physical and emotional vulnerabilities. They
are more likely to have had access to every part of the
victim’s life, including physical belongings (home,
vehicle), their daily routine (work, school), and
information about personal affairs (finances, medical
history).
SEXUAL ASSAULT
Stalking intersects with sexual assault in several
ways. A stalker may threaten to sexually assault the
victim, attempt to get someone else to sexually assault
the victim, or carry out a sexual assault against the
victim. Research shows that 2 percent of people who
are stalked were also sexually assaulted by the
perpetrator, and 31 percent of women who are stalked
by an intimate partner were also sexually assaulted by
that partner.
7, 8
4
Patricia Tjaden and Nancy Thoennes, “Stalking in America: Findings from
the National Violence Against Women Survey,” National Institute for Justice
Centers for Disease Control Research in Brief (1998).
5
Patricia Tjaden and Nancy Thoennes, “Stalking in America: Findings from
the National Violence Against Women Survey,” National Institute for Justice
Centers for Disease Control Research in Brief (1998).
6
McFarlane et al., “Stalking and Intimate Partner Femicide,” Homicide
Studies 3, No. 4 (1999).
7
Katrina Baum et al., “Stalking Victimization in the United States,”
(Washington, DC: Bureau of Justice Statistics, 2009).
8
Patricia Tjaden and Nancy Thoennes, “Stalking in America: Findings from
the National Violence Against Women Survey,” National Institute for Justice
Centers for Disease Control Research in Brief (1998).

RESPONDING TO STALKING: A GUIDE FOR VICTIM ADVOCATES 8
Prior to committing sexual assault, perpetrators may
engage in a variety of stalking behaviors, including
following the victim, repeatedly contacting the victim,
learning the victim’s habits and daily routines, and
gathering personal information about the victim.
These behaviors may be an attempt to identify
potential vulnerabilities or to groom the victim.
After committing or attempting to commit a sexual
assault, the perpetrator may repeatedly contact the
victim in order to:
• Threaten or manipulate them into not reporting
the incident
• Determine what the victim recalls, if drugs or
alcohol were involved
• Frame the incident as consensual
• Maintain social contact
Advocates can help victims of sexual assault identify
stalking behaviors and emphasize how reporting
stalking behaviors may help law enforcement ocers
and prosecutors investigate and successfully prosecute
the crime.
PROPERTY DAMAGE
Another crime that is frequently part of the stalking
pattern of behavior is property damage. Advocates
can assist victims by encouraging them to be aware of
the connection between stalking behaviors and recent
property crimes they have experienced. Although
criminal mischief and vandalism, such as broken
mailboxes or damaged tires may seem commonplace,
they can also be part of a stalking course of conduct.
While broken windshields on every car parked on
a residential street may simply indicate common or
random vandalism, damage that is either specic
to the victim’s belongings or repeated should be
evaluated for stalking involvement.
OTHER CRIMES
Advocates can assist victims by discussing the benets
of explaining to law enforcement the entire context of
the stalking behavior if the victim decides to report
associated crimes. Some of the crimes that may be part
of the stalking course of conduct include:
MAKING THE CONNECTION
Establishing a connection between stalking and
other crimes serves a number of important purposes,
including:
• Supporting the victim’s emotional recovery
• Minimizing the victim’s self-blame
• Demonstrating intentional contact on the part of
the stalker
• Helping law enforcement and prosecutors
understand how other crimes fit into the larger,
targeted course of conduct
• Strengthening the overall criminal justice system
response to stalking
• Nonconsensual
Dissemination of
Intimate Images*
• Protective Order
Violations
• Robbery
• Sexual Assault
• Theft
• Threats
• Trespass
• Utility Theft
• Vandalism
• Vehicle Tampering
• Vehicle Theft
• Voyeurism
• Wiretapping
• Assault
• Burglary
• Child Abuse
• Conspiracy
• Criminal Mischief
• Eavesdropping
• Forgery
• Fraud
• Harassment
• Hate Crimes
• Home Invasion
• Homicide
• Identity Theft
•
Intimate Partner Violence
• Kidnapping
• Mail Theft
*Definition: The Nonconsensual Dissemination of
Intimate Images is the sharing of individuals’
nude photos and videos without their consent.
This may happen on social media or other
websites. While the photos may have been taken
with permission of the victim, perpetrators of
stalking may
use the threat of distribution to
intimidate the victim.

RESPONDING TO STALKING: A GUIDE FOR VICTIM ADVOCATES 9
THE IMPACT OF STALKING ON VICTIMS
Stalking victimization can permeate every aspect of a
victim’s life. Victims of stalking experience many of
the same effects as victims of other crimes, such as
substance abuse, anxiety, and social isolation.
However, victims of stalking also face unique
challenges. Stalking behavior is often persistent and
unpredictable, and can take place over a long period
of time causing repeated trauma. Stalking can affect a
victim’s physical and emotional health, their family
and friends, financial stability, and their job.
IMPACT ON PHYSICAL AND
MENTAL HEALTH
The emotional and physical effects of stalking can
manifest in a variety of ways. The impact of stalking
on the mental and physical health of victims affects
both their ability to safety plan while the stalking is
ongoing as well as their ability to recover after it has
ended. Stalking victims have a higher prevalence of
anxiety, insomnia, social dysfunction, and severe
depression than the general population, especially if
the course of conduct includes being followed or the
destruction of property. Advocates must discuss how
to manage these effects with victims.
Victims may experience a variety of somatic
symptoms, including headaches, general aches and
pains, feelings of weakness or numbness, sleeping
too much or too little, nightmares and persistent
dreaming, and changes in weight. Increased anxiety,
common among stalking victims, is also connected to
physical symptoms, including shaking, chest pains,
and panic attacks. The physical manifestations of
stress extend to a lowered immune system response
and influence current or underlying medical
conditions. Support from a medical professional,
such as a therapist or general practitioner, may help
the victim to cope with the physical and mental
effects they are experiencing.
9
9
Eric Blauuw et al. “The Toll of Stalking,” Journal of Interpersonal
Violence 17, no. 1(2002).
IMPACT ON PERSONAL
RELATIONSHIPS
Stalking aects not only victims, but also their family,
friends, and coworkers. Some stalking perpetrators
may attempt to contact the victim’s family members or
friends for information, such as the victim’s location,
workplace, or contact information.
Other perpetrators may ask third parties to contact
or follow the victim for them. This practice is called
proxy stalking. Perpetrators of intimate partner
stalking may also attempt to use children to stalk.
Because many proxy stalkers are part of the victims’
support network, victims may nd it challenging
to reach out for support. Victims may be reluctant
or not want to involve people they know out of
embarrassment or shame. They may fear the
perpetrator will act out against the third party if they
attempt to ask for help. In addition, they may be
unsure about the safety of the technology they use to
communicate with their support network. Advocates
must encourage stalking victims to think broadly
about whom they trust and how to safely
communicate with their support system about their
situation.
• Abuse of drugs or alcohol
•
Inability to study
•
Anger
•
Irritability
•
Anxiety
•
Loss of confidence
•
Confusion
•
Loss of relationships
•
Depression
•
Minimization
•
Economic losses
•
Nightmares
•
Embarrassment
•
PTSD
•
Emotional numbness
•
Self-blame
• Fatigue
• Sexual dysfunction
• Fear
• Shame
• Flashbacks
• Shock
• Frustration
• Sleep disturbances
• Social isolation
• Guilt
• Suicidal ideation
• Hypervigilance
• Inability to accomplish
daily tasks
• Inability to concentrate
• Weight changes
COMMON EFFECTS OF STALKING

RESPONDING TO STALKING: A GUIDE FOR VICTIM ADVOCATES 10
IMPACT ON FINANCES
Stalking often results in direct and indirect economic
losses for the victim that occur in a variety of ways.
• Property damage – cost of replacement or repairs
for damage caused by the perpetrator
• Legal processes – court fees, attorney fees, costs to
travel to court appointments, and child care for
times when caregivers are in court
• Medical bills (mental and physical health) – stalking
victims will utilize health services at a higher rate
than victims of domestic violence alone
10
• Technology – cost to replace technology that may
have been compromised by the stalker
• Relocation – if the victim chooses to move to get
away from the perpetrator
• Lost wages
Advocates should be prepared to discuss options for
nancial assistance that support the victim’s safety. See
Crime Victim Compensation on page 17.
IMPACT ON THE WORKPLACE
Stalking can affect victims’ work in a variety of ways.
Victims of stalking may take time off to go to court,
meet with an advocate, or take care of their mental or
physical health, resulting in lost wages if they do not
have paid leave.
11
Many victims do not report their stalking
victimization to their employer, or may only report to
trusted coworkers rather than managers or the human
resources department. The victim’s supervisor may
not understand the victim’s behavior (e.g., distracted
or declining performance) and may wrongfully
conclude that the victim is a poor employee, resulting
in discipline or termination. In some cases, employers
who know an employee is being stalked may be
concerned about a risk to the workplace and ask the
victim to resign.
As an advocate, your role is to help victims identify
and weigh the pros and cons of discussing the stalking
with their employer and to help them contact an
attorney if they are wrongfully terminated. Victims of
stalking may have protections, and advocates can
assist by learning more about available options at
http://workplacesrespond.org.
10
Logan, T., Walker, R., Hoyt, W. and Faragher, T. “The Kentucky Civil
Protective Order Study: A Rural and Urban Multiple Perspective Study of
Protective Order Violation Consequences, Responses, and Costs.” 2009.
Washington, DC: National Institute of Justice, U.S. Department of Justice.
11
Many states now have laws to protect victims of domestic violence and
stalking by mandating employers oer paid sick leave for victims to attend
court hearings. Yet, in some states, the stalking may aect their job security.

RESPONDING TO STALKING: A GUIDE FOR VICTIM ADVOCATES 11
THE ADVOCATE
ROLE IN
ASSISTING
STALKING
VICTIMS

RESPONDING TO STALKING: A GUIDE FOR VICTIM ADVOCATES 12
COMMON VICTIM REACTIONS AND
RESPONSES
Reactions to stalking are as diverse as victims
themselves. As a group, however, victims share
several common responses:
• Minimizing: Victims may minimize individual
stalking behaviors and the risk the offender poses.
They may isolate events—focusing on a recent, less
serious behavior instead of connecting it to more
serious violations in the past. For example:
• “They’re only text messages.”
• “He would never really harm me.”
• Avoiding family or friends: Victims may avoid
family and friends because they feel embarrassed,
ashamed, or responsible for what is happening. In
many instances, the stalker is someone known to the
victim, their family, and their friends. They may
avoid contact with loved ones in order to also avoid
the perpetrator. They may be afraid they won’t be
believed or that their friends and family will take
sides against them. Victims may also want to keep
loved ones safe from the stalker.
• Negotiating for safety: Victims may negotiate with
the perpetrator for their own or others’ safety. They
may agree to demands the perpetrator makes or
maintain contact in an effort to prevent additional
harm.
• Taking steps to improve their personal security:
Many victims engage in informal safety planning on
their own to cope with the perpetrator’s tactics and
behaviors. For example, they may take a different
route to school or work, temporarily stay with a
friend, or change the locks on their door.
As an advocate, it is important to recognize and
validate any steps victims have taken to stay safe, oer
guidance on additional measures they could take, and
support their actions moving forward.
SAFETY PLANNING
Advocates can help victims strategize about how to
more safely respond to stalking by creating a safety
plan. A safety plan is a combination of suggestions,
concrete steps, and strategic responses designed to
increase the victim’s safety during specific
situations. Every victim’s safety plan is different—
tailored to their unique circumstances—and every
perpetrator will respond differently to those safety
tactics. It is
important to keep in mind—and
communicate to the victim—that safety plans do not
guarantee a victim’s safety, but they can greatly
increase it.
Effective safety plans are:
• Flexible – Many options are available for any given
scenario. Victims are able to evaluate which option
best fits their current situation. The plan can also be
adjusted if the perpetrator’s behavior changes.
• Comprehensive – The safety plan considers every
aspect of the victim’s life, including family and
friends, children, school, work, and daily routine.
• Contextual – The plan should account both for what
the victim is currently experiencing and for the
pattern of previous behavior.
To help craft an effective safety plan, advocates can:
• Listen and ask questions non-judgmentally
• Help identify the victim’s specific needs and goals
• Discuss and analyze risks
• Explore strategies and resources
• Provide information and options

RESPONDING TO STALKING: A GUIDE FOR VICTIM ADVOCATES 13
SAFETY-PLANNING SUGGESTIONS
Below are suggestions for safety planning, including if
a victim is currently in a relationship with the
perpetrator, has recently ended the relationship,
has never had an intimate relationship with the
perpetrator. Advocates should also consider if the
victim is seeking services for the first time. Remember
to evaluate each component with regard to (A) the
context of the situation and (B) how the perpetrator
will likely respond, according to the victim.
DISENGAGEMENT
In many cases, it is best for stalking victims to
completely disengage with the perpetrator to stay
safe. For some perpetrators of stalking, any contact
may reinforce their behavior, even if the interaction is
negative. It may be best for a victim to let every call
from a perpetrator go to voicemail rather than to
answer and ask the perpetrator to stop calling. The
perpetrator may see this contact as evidence their
methods have been successful, rather than a rejection.
Additional advocacy and safety planning may be
required to address the following circumstances:
• Children – If the victim and perpetrator share
custody of any children, the victim is unlikely to be
able to completely disengage.
• Safety – For some victims it may be safer to remain
in contact. A victim may answer a phone call from
the perpetrator to ward off an escalation in behavior,
such as the perpetrator showing up at the victim’s
house.
• Small communities – In rural areas or closed
communities (such as college or university
campuses, military property, or tribal lands), it may
be impossible to avoid seeing the perpetrator.
DOCUMENTATION
Victims should be encouraged to document all
stalking behaviors and preserve any evidence such as
emails, text messages, or gifts – even if they do not
intend to move forward with criminal charges. If the
victim decides to report the stalking to law
enforcement or apply for a protective order, this
documentation is an important component of
demonstrating the course of conduct. It also provides
victims, service providers, and law enforcement
officers with an overview of the stalking behaviors
and timeline so they can identify any escalation in
behaviors. A sample stalking log is included here:
www.stalkingawareness.org/documentation-log/
To stay safe while documenting behaviors, victims
need to consider:
• Computer documentation – Is the computer safe
from spyware that could give the perpetrator access
to all of the documents, websites, emails, and other
information the victim is using?
• Paper documentation – Can several copies be stored
in different places that the perpetrator cannot
access? These locations could be a friend or family
member’s house, the victim’s workplace, a sports
locker, or a safety deposit box.
Emma is sitting in your office with her two children, Noah and Mason. Lucas, her ex-boyfriend and the
father of her children, threatened to hurt her children last month if she did not move back in with him.
Since then, he has been repeatedly texting and calling her cellphone and showing up unexpectedly at her
children’s daycare. Before they separated, he monitored her location using her cell phone. Emma wants to
know what she can do to be safe.
FLEXIBLE – It is important that Emma and her children have somewhere safe to stay. She can stay in her
home if she feels safe there. But it’s also important to have a backup plan. Can they stay with a relative or
a friend for a few nights with little notice? Can Noah and Mason attend a different daycare or stay with a
relative or friend for a few days? Is there a local shelter where they can stay? Do they have enough money
to stay in a hotel?
COMPREHENSIVE – Can she alter her work schedule so that Noah and Mason go to daycare at a
different time? Is she comfortable talking to the daycare teachers about what is happening? Do Emma
and Lucas have a parenting plan in place? Has she discussed the situation with her employer?
CONTEXTUAL – Lucas appears to use technology as a way to track Emma. The best way to determine
potential barriers to safety is to ask victims if they would like to share any concerns. Doing so will assist
in safety planning as well as the search for services. Can she talk to her employer about security
protection for her computer?

RESPONDING TO STALKING: A GUIDE FOR VICTIM ADVOCATES 14
Documentation should include:
• Time of incident
• Location of incident
• Full names of any witnesses
• Incident number if a police report was taken
• Detailed description of what happened
Some victims may be reluctant to document the
stalking behaviors. They may feel unsafe or find the
process upsetting. Be sure to discuss with victims the
fact that any documentation or evidence they provide
to law enforcement could be introduced as evidence
in court or inadvertently shared with the perpetrator.
Victims should not include any information that they
do not want the perpetrator to access.
EVIDENCE
Examples of evidence that should be documented and
maintained include:
•
Letters or notes written by the perpetrator to the
victim
•
Objects sent to or left for the victim, including “gifts”
•
Voicemail messages left by the perpetrator
•
Evidence of phone tapping or tampering
•
Emails, preserved electronically and printed out with
an expanded header showing the IP address
•
Telephone records
•
Text records
•
Screen shots of social network posts to or about
the
victim
•
Screen shots of other online posts to or about the
victim, including the website address (also known as
a “URL”)
•
Photos or videos
posted online of or about the victim
(download a copy and document any active URLs)
SUPPORT SYSTEM
For most stalking victims, having a few people they
can trust and rely on is essential to their ability to
cope and recover from the crime. Advocates can help
victims think broadly about who in their network can
provide that support. Some victims may want to
consider implementing a daily safety check with a
member of their support system. This can be as simple
as a text message every day letting the person know
they are okay. This support person may be someone
well-known to the victim, a casual acquaintance, or
professionally connected, including:
• Family members, such as siblings, cousins, aunts,
and uncles
• Friends
• Neighbors
• Members of their house of worship
• Members of other affiliated, community, or
professional groups
• Coworkers
• Medical or legal professionals
• Advocates
For some victims this exercise may be challenging.
They may wish to keep people safe by not involving
them or they may be reluctant to trust anyone,
especially if the perpetrator knows all of their friends
and family.
REPORTING TO POLICE
Advocates can help victims think about whether they
want to report stalking to law enforcement and how
to stay safe if they choose to report. While reporting
to law enforcement often seems like an obvious step,
it may not be safe for a victim to report the crime at
the time of the incident. Instead, they may choose to
file
a report on a later, safer date. Sometimes,
reporting stalking can cause the perpetrator to
escalate the behavior, creating an increased level of
danger for the victim.
If a victim decides to report to the police, advocates
can support their decision by helping them
understand what to expect. Victims can prepare by:
• Expecting law enforcement officers to ask specific
and intimate questions such as “Does the stalking
cause you to feel fear?”
• Identifying incidents that demonstrate the course of
conduct
• Outlining the events to ensure clear communication
• Bringing any related documentation of the stalking,
such as the stalking incident log
• Understanding that law enforcement may or may
not arrest the perpetrator
• Remembering investigations can take a long time

RESPONDING TO STALKING: A GUIDE FOR VICTIM ADVOCATES 15
SAFETY PLANNNG TIPS
1. Think about all of the people potentially affected:
children, grandparents, pets, coworkers, etc.
2. Keep in mind both short-term and long-term safety:
a. Short-term safety can be a few weeks to a few
months, depending on the situation and the
persistence of the perpetrator.
b.
Long-term safety planning may not be
necessary for every victim but is important to
discuss, as stalking behavior continues for an
average of two years.
3. Provide resources for the victim to access at any
time, such as a 24-hour hotline.
a. Check for local resources first.
b. If there are no local 24-hour hotlines in
your area:
i. National Domestic Violence Hotline:
1-800-799-7233 or chat online here
https://www.thehotline.org.
ii. National Sexual Assault Hotline (RAINN):
1-
800-656-4673 or chat online here
https://hotline.rainn.org/online.
c. VictimConnect Resource Center can assist with
safety planning and resources for victims of
stalking:
1-855-484-2846 or chat online here
https://chat.victimsofcrime.org/victim-connect/.
SAFETY BY LOCATION
IN THE HOME:
• Avoid bathrooms, the kitchen, the garage and other
areas where weapons may be found when the
perpetrator is in the home.
• Identify which rooms have strong doors, locks, and
windows that open.
• Install an alarm system and/or motion detector;
some security companies will provide these for free
or a discounted rate to victims of stalking.
• Talk to neighbors: ask them to call 911 if they see
the perpetrator or hear something concerning; if
comfortable sharing, give them copies of protective
orders.
AT WORK:
• Change telephone numbers, location, and hours if
possible.
• Provide copies of protective orders to supervisors.
• Park close to the office door or ask someone to walk
them to their car.
• Develop an office or work-escape plan.
• Talk with security guards and receptionists about
who is allowed to visit; provide a photograph of the
perpetrator; ask front-desk personnel to call before
letting someone into their office.
WITH CHILDREN
If the victim has children, they may be affected by
the stalking, regardless of their relationship to the
perpetrator. Victims of stalking with children
should consider the following:
• Identifying safe places for the children to hide if the
perpetrator approaches them or the victim.
• Teaching the children how to call 911, and giving
them permission to do so.
• Discussing who the children can go to for help
(e.g., family members, neighbors, law enforcement).
• Providing copies of protective orders to schools,
daycares, and other care providers.
• Making sure every person who takes custody of the
children knows who else is allowed to pick them up.
• Obtain advice about civil legal remedies to protect the
children.

RESPONDING TO STALKING: A GUIDE FOR VICTIM ADVOCATES 16
PROTECTION ORDERS/
RESTRAINING ORDERS
A protective order is a legal order issued by a state court
that requires one person to stop harming and/or
contacting another. Each state may have several types of
protective orders—such as civil protective orders,
criminal protective orders, or restraining orders—
and they may have different names. (For example,
Pennsylvania has “protection from abuse” orders).
Some protective orders are specific to domestic and
intrafamilial violence, while others are broader, covering
stalking, harassment, sexual assault, and other types of
abuse. Civil protection orders do not require that the
perpetrator be charged or convicted; as long as the
behavior, the relationship between the parties, and the
harm or threat to the victim come within the legal
requirements, the court can issue an order. Violations of
the civil protection order are typically criminal offenses.
A protection order is one possible tool a victim can
use to help stop the stalking and enhance their safety.
However, they are not effective in every case and may in
fact escalate the stalking behavior in some cases.
To help victims of stalking understand the risks and
benefits of seeking a protection order, consider the
following:
• How do they anticipate the perpetrator will respond
to the protection order?
•
•
How and when will the perpetrator be served with
the protection order?
Will it be dangerous for the victim to appear in
court because the perpetrator will know where the
victim is?
• How will the process aect any current or future
family law proceedings?
• Will the victim call law enforcement if the
perpetrator violates the order?
For a protection order to be most eective, victims
should also know:
• Enforcement may be easiest if they carry a copy of the
protection order with them wherever they go.
• They should provide copies of the order to
employers, schools, babysitters, landlords, neighbors,
family members, and others, especially if the order
prohibits the perpetrator from being at certain
locations or contacting children.
• Orders of protection must be honored in other
jurisdictions. For more information, see The National
Center on Protection Orders and Full Faith and
Credit, a program of the Battered Women’s Justice
Project.
http://www.bwjp.org/our-work/projects/protection-
orders.html
• Violations of a civil protection order may permit or
require the police to make an arrest if they find
probable cause to believe the offender has violated
the order.
• An attorney who represents the perpetrator may ask
the victim to agree to mutual orders in an effort to
discredit the victim. This means that both parties
would have a protection order against the other. The
victim does not have to do this in order to obtain an
order that prohibits the stalking offender from
continued stalking. Victims should seek legal counsel
before agreeing to such mutual order. The existence
of such an order may allow for the perpetrator to file
criminal charges against the victim.
Advocates have an important role in helping victims
weigh the dierent benets and drawbacks regarding
protection orders as well as guiding them through the
court system and ling process.

RESPONDING TO STALKING: A GUIDE FOR VICTIM ADVOCATES 17
ADDRESS CONFIDENTIALITY PROGRAMS
Address Confidentiality Programs (ACPs) allow
victims of stalking, sexual assault, domestic violence,
or other types of crime to receive mail at a substitute
address. ACPs keep the victim’s actual address
private and prevent oenders from locating the
victim through public records. Mail is sent to the
legal substitute address, often a post
office box, and
then forwarded to the victim’s actual address. The
substitute address can be provided whenever the
victim’s address is required by a public agency. While
Address Condentiality Programs can assist with
a victim’s safety, they do not guarantee their safety.
Victims can increase their safety by:
• Limiting the number of people they tell about
their address, doing their best to ensure that these
individuals are trustworthy and discreet.
• Abiding by the terms of the ACP. Some ACPs will
remove a participant from the program if they
violate the terms.
• Advocates can help victims understand the terms of
the program in their particular state and how it
operates. However, not every state has an Address
Confidentiality Program. If your state does not have
a program, it is essential that you discuss other ways
for victims to make it more difficult for the offender
to locate them.
CRIME VICTIM COMPENSATION
One possibility for financial assistance is Crime
Victim Compensation. Every state has a state-level
Crime Victim Compensation program. Victims of
stalking who apply to crime victim compensation
may be eligible to have some of their crime-related
expenses reimbursed, such as lost wages, medical
bills and mental health counseling, and lock changes.
Some states may assist with relocation expenses for
safety.
Each program, however, has different requirements
and benefits. Most states require a police report, but
some will also accept a protection order, a SANE
exam (rape kit), or a neglect petition (for victims of
child abuse and neglect). For more information on
the program in your state, visit the National
Association of Crime Victim Compensation Boards.
http://www.nacvcb.org/
Advocates can help victims of stalking navigate this
process by understanding the documents, deadlines,
and reimbursable expenses for their state’s program.

RESPONDING TO STALKING: A GUIDE FOR VICTIM ADVOCATES 18
PRACTICE

RESPONDING TO STALKING: A GUIDE FOR VICTIM ADVOCATES 19
CASE SCENARIOS
For each case scenario, think about the following questions and how you would support this victim
with the resources in your community:
• Which risk factors are present?
• Does the perpetrator pose a threat?
• If so, to whom?
• In your professional capacity, how would you work with the victim at this point?
• What questions would you like to ask the victim? What information would be helpful?
• What safety concerns do you have and how can they be addressed?
• What options and resources would you provide to the victim?
• Would collaborating with other agencies or organizations to support this victim be useful?
1. DEREK AND JAMES
Derek comes to you to discuss a confrontation with his
ex- boyfriend, James, whom he dated for about 5
months. They broke up last month, but the break-up
didn’t go well.
This morning when Derek left his apartment, James
was parked in front of the building. James approached
him and started yelling, saying he was still in love
with Derek and knows he is still in love with him.
James told Derek it didn’t matter if he tried to ignore
him, he would always be there to show him how
much he cares. James left when a neighbor came out to
see if Derek was okay.
Derek goes on to tell you that things were okay the
first few months of their relationship, but then James
started demanding more of his time. James wanted the
two of them to spend all of their free time together and
would get upset when Derek wanted to spend time
with his friends or family. James would talk about
spending the rest of their lives together, even though
Derek made it clear that he wasn’t looking to settle
down at this point in his life. He tried talking to James
several times about keeping it casual and James would
back off for a few weeks before reverting to his
insistence on a permanent relationship. Derek then
decided that he and James clearly wanted different
things from the relationship and broke up with him.
Since they broke up, James keeps trying to stay in
touch with Derek. Derek gets 15-20 texts and emails
from James every day. James kept messaging him
while he was at work until he blocked him. James
then sent him an angry, threatening email. James
keeps showing up at the same places Derek is. At first
Derek thought this was just a coincidence, but now
he’s not so sure.
Consider:
A.
James keeps showing up at the same locations
as Derek; he may be tracking him through
spyware on his cell phone.
B.
A protection order may be a good option for
Derek, but it may also cause the behavior to
escalate. It is important to examine the pros
and cons of
filing for one.
C.
Derek’s neighbor has demonstrated she cares
about his well-being. Derek could ask her to
call the police if she sees James outside the
apartment again.

RESPONDING TO STALKING: A GUIDE FOR VICTIM ADVOCATES 20
2. JANET
Janet calls your hotline regarding items that have gone
missing from her apartment. She tells you that she is
70 years old and lives alone. Over the last few months,
objects in her apartment have disappeared or have
been moved to a different location in the apartment.
She describes the items as being of little value to her,
items such as a notepad or a houseplant.
She has called law enforcement several times to report
the missing items, but they don’t seem to believe her.
They have come to the apartment three times, but the
last time they didn’t take a report. Law enforcement
told Janet that there was no sign of forced entry.
Janet has told her adult children about the problem
and they have started talking about moving her to an
assisted living facility. She doesn’t want to live in a
facility so she has stopped telling her children when it
happens.
Consider:
A. The law enforcement officers who spoke with
Janet seem to have perceiv ed Janet as confused
and forgetful. When you talk to her, she doesn’t
sound confused, just scared.
B.
You remember a similar case from a few years
ago. Using
a hidden camera, a detective caught a
man using a key to get into an older victim’s
home and move her things.
C. Janet is feeling alone, her safety plan should
include reaching out to her family. As a family,
they could meet
with an advocate to discuss her
possible options.
3. MACKENZIE AND DAVID
Mackenzie is being stalked by her neighbor whom she
has known most of her life. They live on nearby tribal
lands. David started texting her repeatedly several
months ago, asking her to go on a date with him.
Mackenzie tells you that she had a boyfriend at
the time which she told David. He kept texting her
anyway. When Mackenzie and her boyfriend broke
up, David started calling her. Mackenzie told him she
wasn’t interested in dating him, but he continued to
call her. Last week, he started showing up at her work
around lunch time, asking her to go to lunch with
him. She also started getting texts and phone calls
from members of David’s family pressuring her to
date him. Mackenzie tells you that she thinks his
friends and family are helping him keep track of her.
It’s the type of town where everyone knows everyone.
Last night, David was sitting on her front porch when
she got home and wouldn’t leave. Mackenzie didn’t
feel safe opening her door when he was there so she
left and spent the night at her parents’ house. She is
considering moving so that she no longer lives next
door to him.
Consider:
A. Help Mackenzie think through her support
network Is there someplace she can stay that is
safe? Who can she trust?
B. Does she think a protection order would be
effective or would he ignore it? If she thinks he
would listen to it, it may also protect her from
his family as the order could bar 3rd party
contact.
C. If Mackenzie decides to move, she could apply
to participate in an address confidentiality
program depending on her state.
4. MARCUS
Marcus is a college professor at a small liberal arts
university in the same city where your program is
based. One of his students, Katie, has been visiting his
office hours a lot lately. She didn’t do very well on the
last exam and she was visibly upset about it when he
returned the tests to the class last month.
She emails him multiple times a day and has started
showing up at his favorite morning coffee shop several
times a week. Yesterday, she told him that if she didn’t
do better on the next test, he would be sorry.
Consider:
A. Marcus works for a university which means an
issue with a student could have repercussions
on his career. If Marcus is comfortable talking
with his supervisor about this, it may help him
protect his job.
B. Marcus has a fairly regular routine. He can
change it up by going to a different coffee
shop and working in a different office or at the
library.

RESPONDING TO STALKING: A GUIDE FOR VICTIM ADVOCATES 21
CONCLUSION
Stalking happens much more frequently than most
people realize and is often connected to many other
crimes. It is vital that victim advocates are able to
identify stalking behaviors and build eective safety
plans with victims of stalking. We hope this guide
will help you identify stalking behaviors, the barriers
stalking victims face, and solutions that enhance
their safety. Please visit our website for additional
information.
The Oce on Violence Against Women supported the
development of this product under award 2017-TA-
AX-K074. The opinions and views expressed in
this document are those of the authors and do not
necessarily represent the ocial position or policies
of the Oce on Violence Against Women of the U.S.
Department of Justice.

1000 Vermont Ave NW, Suite 1010 | Washington, DC 20005 | (202) 558-0040 | stalkingawareness.org
@FollowUsLegally

STALKING
PREVENTION,
AWARENESS,
AND RESOURCE
CENTER
Addressing Stalking: A Checklist for Domestic and
Sexual Violence Organizations
Because there are very few stalking-specific service providers, stalking victims rely on domestic and/or
sexual violence programs to assist them with safety planning and resources. In reviewing your agency’s
response to stalking, consider the following questions:
• Does your organization provide services to victims of stalking?
• If so, how easy is it for a stalking victim to know they can seek services from your organization?
For instance, is stalking specifically mentioned in your outreach materials?
• Do your organization’s services address the needs of all victims of stalking – including those
stalked by someone who is not an intimate partner?
Please use the checklist below assess your agency’s efforts to respond to stalking.
Of course, different agencies vary in mission, scope, and capacity, so not all categories or suggestions
will be relevant to or feasible for every service provider.
Organization Mission and Values
❑
Serving victims of stalking is included as part of your organization’s statement of mission and
values.
Website
❑
“Stalking” is mentioned on your website as a form of violence your agency addresses.
❑
Your website links to Victim Connect (the referral hotline for victims of crime,
including stalking).
❑
Your website provides definitional information/fact sheets on stalking (see these resources).
❑
Your website provides a link to a stalking log that victims can use to document evidence of
stalking.
❑
Your website features stories that focus on or include stalking.
❑
Your website notes that January is National Stalking Awareness Month (resources here).
Social Media
❑
Your organization participates in National Stalking Awareness Month in January by sharing
relevant posts on your social media platforms.
❑
Your social media platforms feature stories that focus on or include stalking.
❑
You post facts, statistics, and new studies about stalking with some frequency.
❑
You follow SPARC (@FollowUsLegally) on social media and share relevant
posts/information.

STALKING
PREVENTION,
AWARENESS,
AND RESOURCE
CENTER
Print Materials
❑
Promotional and awareness materials (fliers, posters, brochures, postcards, etc.) state that
you provide services to victims of stalking.
❑
You engage in public awareness campaigns that highlight the crime of stalking.
❑
If you provide fact sheets, brochures, or other print resources for distribution by local law
enforcement or other collaborative partners, you include resources devoted to stalking.
Staff Training
❑
Victim advocates, hotline staff, and shelter staff receive regular training and information
about stalking victimization.
❑
Your organization regularly seeks and participates in trainings and webinars on the topic of
stalking.
❑
Your staff is familiar with safety planning strategies for victims of stalking (some suggestions
here).
❑
Staff are aware of resources relevant to victims of stalking, such as
www.stalkingawareness.org and NNEDV Safety Net (for technology safety).
Serving Victims and Survivors
❑
Staff are able to identify stalking even when it is not identified as such by the victim. For
example, if a victim states “my ex has gotten creepy,” staff would be alert to the potential of
a stalking situation.
❑
Staff are knowledgeable about what services they can and cannot provide to victims
of stalking.
❑
Staff use the Stalking Harassment Assessment Risk Profile (SHARP) when appropriate
– a research-based assessment tool designed to assess risk when stalking behavior is
present.
❑
Staff work to accommodate the immediate safety needs of all victims of stalking,
including those being stalked by someone who is not an intimate partner (for
example, those stalked by a coworker or neighbor).
❑
If your agency is unable to provide assistance to those stalked by someone other than
an intimate partner, you have identified one or more other agencies that can assist.
❑
Court advocacy staff are able to assist with civil orders of protection specific to
stalking or harassment (if applicable) and know how to highlight any stalking behavior
that occurs within the context of an intimate relationship for purposes of obtaining a
domestic violence protection order.
❑
Your mental health referral network includes professionals who have expertise
working with victims of stalking.

STALKING
PREVENTION,
AWARENESS,
AND RESOURCE
CENTER
Community Education
❑
You provide community training on stalking (ready-to-teach programs available here).
❑
When educating on intimate partner violence tactics, you use the word “stalking” to describe
controlling behaviors that are stalking such as surveillance or constant phone calls or text
messaging.
Partnerships
❑
You have identified and built collaborative relationships with organizations and are able to
provide a warm referral to stalking victims.
❑
You include stalking in your coordinated response efforts.
❑
Your organization provides training to law enforcement, mental health practitioners, attorneys,
probations/corrections officers and other relevant partners in addressing stalking.
❑
You share information with your partners about relevant trainings or webinars that address
stalking.
For additional assistance in ensuring your program is accessible to stalking victims, please contact
SPARC at [email protected] or visit our website at www.stalkingawareness.org.
This project was supported by Grant No. 2017-TA-AX-K074 awarded by the U.S. Department of Justice, Office on Violence Against Women (OVW). The
opinions, findings, conclusions, and recommendations expressed are those of the authors and do not necessarily reflect the views of OVW.

STALKING RESPONSE STRATEGIES
FOR COLLEGE CAMPUSES
This project was supported by Grant No. 2017-TA-AX-K074 awarded by the Office on Violence Against Women, U.S. Department of Justice. The opinions, findings,
conclusions, and recommendations expressed in this publication/program/exhibition are those of the author(s) and do not necessarily reflect the views of the Department
of Justice, Office on Violence Against Women.
1000 Vermont Avenue NW, Suite 1010 | Washington, DC 20005 | (202) 558-0040 | www.stalkingawareness.org
@FollowUsLegally
DID YOU KNOW
Stalking is a violation of student conduct codes and Title IX, and is a crime under the laws
of the 50 states, District of Columbia, U.S. Territories, and Federal government. Adults
18-24 years old experience the highest rates of stalking, making it vital for colleges to
appropriately address stalking on campus and ensure services are accessible to all stalking
victims. Campuses face the challenges of high prevalence rates and predictable victim
schedules that make it relatively easy for stalkers to access victims.
The majority of campus victims are stalked by someone they know and most stalkers are
fellow students. Stalking interferes with victims’ academics and extracurricular activities. In
addition to serious and long-lasting emotional and psychological harm, stalking can
involve severe — even lethal —violence. Campuses that understand the nature and
dynamics of stalking, the impact of stalking on victims, and the jurisdictional complexities
of stalking cases can support victims and hold stalkers accountable.
HOW CAMPUS PROGRAMS CAN HELP
1. Recognize that stalking is a pattern of behavior, and a stalking victim’s level of fear and
need for resources and assistance may vary and change based on the stalker’s behaviors.
2. Listen closely to victims — even if what they say sounds unbelievable — and refer them
to seek additional support. Some college employees are mandated to report stalking
while others may not be. Ensure that the campus community is aware of who is and is
not a confidential assistant.
3. Documentation can be extremely helpful in stalking cases. Victims could consider using
this campus documentation log.
4. Support victims by providing appropriate accommodations in their academics, housing,
extracurricular activities, and/or whatever else they need to feel safe.
5. Collaborate with other programs on campus, external support services, and the criminal
and civil justice systems to protect victims and hold stalkers accountable.
6. Investigate incidents to see if they establish a pattern of behavior and are a violation of
campus policies.
While legal
definitions of
stalking vary from
one jurisdiction to
another, Title IX and
the Clery Act have a
good working
definition:
Engaging in a course
of conduct directed
at a specific person
that would cause a
reasonable person to
(1) Fear for the
person’s safety or the
safety of others; or
(2) Suffer substantial
emotional distress.

STALKING VICTIMIZATION
• An estimated 6-7.5 million people are stalked in a one year
period in the United States.
• Nearly 1 in 6 women and 1 in 17 men have experienced stalking
victimization at some point in their lifetime.
• Using a less conservative definition of stalking, which considers
any amount of fear (i.e., a little fearful, somewhat fearful, or
very fearful), 1 in 4 women and 1 in 13 men reported being a
victim of stalking in their lifetime.
• About half of all victims of stalking indicated that they were
stalked before the age of 25.
• Stalkers use many tactics including:
Approaching the victim or showing up in places when the victim
didn’t want them to be there; making unwanted telephone calls;
leaving the victim unwanted messages (text or voice); watching or
following the victim from a distance, or spying on the victim with
a listening device, camera, or GPS.
* Source for the above stats: Smith, S.G., Zhang, X., Basile, K.C., Merrick, M.T., Wang,
J., Kresnow, M., Chen, J. (2018). The National Intimate Partner and Sexual Violence
Survey (NISVS): 2015 Data Brief. Atlanta, GA: National Center for Injury Prevention
and Control, Centers for Disease Control and Prevention.
• The majority of stalking victims are stalked by someone they
know. Many victims are stalked by a current or former intimate
partner, or by an acquaintance.
• People aged 18-24 have the highest rate of stalking victimization.
** Source for the above stats: Catalano, S., Smith, E., Snyder, H. & Rand, M. (2009).
Bureau of Justice Statistics selected findings: Female victims of violence. Retrieved
from http://www.bjs. gov/content/pub/pdf/fvv.pdf.
• Almost half of stalking victims experience at least one unwanted
contact per week.
• 11% of stalking victims have been stalked for 5 years or more.
• 1 in 4 victims report being stalked through the use of some form
of technology (such as e-mail or instant messaging).
• 10% of victims report being monitored with global positioning
systems (GPS), and 8% report being monitored through video
or digital cameras, or listening devices.
*** Source: Katrina Baum et al., “Stalking Victimization in the United States,”
(Washington, DC: Bureau of Justice Statistics, 2009).
IMPACT OF STALKING ON VICTIMS
• 46% of stalking victims fear not knowing what will happen next.
• 29% of stalking victims fear the stalking will never stop.
• 1 in 8 employed stalking victims lose time from work as a result
of their victimization and more than half lose 5 days of work
or more.
• 1 in 7 stalking victims move as a result of their victimization.
**** Source: Katrina Baum et al., “Stalking Victimization in the United States,”
(Washington, DC: Bureau of Justice Statistics, 2009).
• Stalking victims suer much higher rates of depression,
anxiety, insomnia, and social dysfunction than people in the
general population.
****Source: Eric Blauuw et al., “The Toll of Stalking,” Journal of Interpersonal Violence, 17,
no. 1 (2002):50-63.
STALKING OFFENDERS
• 2/3 of stalkers pursue their victims at least once per week, many
daily, using more than one method.
• 78% of stalkers use more than one means of approach.
• Weapons are used to harm or threaten victims in 1 out of 5 cases.
• Almost 1/3 of stalkers have stalked before.
• Intimate partner stalkers frequently approach their targets,
and their behaviors escalate quickly.
****Source: Kris Mohandie et al.,“The RECON Typology of Stalking: Reliability and
Validity Based upon a Large Sample of North American Stalkers,” Journal of Forensic
Sciences, 51, no. 1 (2006).
STALKING LAWS
• Stalking is a crime under the laws of 50 states, the District of
Columbia, the U.S. Territories, and the Federal government.
• Less than 1/3 of states classify stalking as a felony upon first
oense.
• More than 1/2 of states classify stalking as a felony upon second
or subsequent oense or when the crime involves aggravating
factors.
• Aggravating factors may include: possession of a deadly weapon,
violation of a court order or condition of probation/parole, victim
under 16 years, or same victim as prior occasions.
STALKING FACT SHEET
WHAT IS STALKING?
?
While legal definitions of stalking vary from one jurisdiction
to another, a good working definition of stalking is: a course
of conduct directed at a specific person that would cause a
reasonable person to feel fear.
@FollowUsLegally
STALKING PREVENTION, AWARENESS,
AND RESOURCE CENTER
This project was supported by Grant No. 2017-TA-AX-K074 awarded by the Office on Violence Against Women, U.S. Department of Justice. The opinions, findings,
conclusions, and recommendations expressed in this publication/program/exhibition are those of the author(s) and do not necessarily reflect the views of the Department
of Justice, Office on Violence Against Women.
1000 Vermont Ave NW, Suite 1010 | Washington, DC 20005 | (202) 558-0040 | stalkingawareness.org
COLLEGE STUDENT STALKING VICTIMIZATION
• Between 6% and 39% of college students report being stalked
since entering college.
A
• College students at higher risk for experiencing stalking include:
o Women
B
o Students of color
C
o Sexual minority and gender non-conforming college
students (LGBTQ+)
D
o Students with disabilities
E
o Students living o campus
F
o Younger students
G
•
Among undergraduates stalked by an intimate partner:
H
o 32% were sexually assaulted the prior academic year
o 40% experienced co-occurring coercive control
o 27% experienced co-occurring threats for a partner to hurt
themselves, the victim, or someone the victim loves
o 11% experienced co-occurring physical assault by an
intimate partner
•
43% of college stalking victims who meet the legal criteria of
‘stalking’ do not identify their experience as ‘stalking’.
I
DISCLOSURE AND HELPSEEKING
Among college stalking victims:
J
•
92% tell friends and/or family.
•
29% contact a program or resource for help, more than victims
of sexual harassment (12%) or IPV (19%).
o Transgender, nonbinary, genderqueer, or gender
questioning (33%) are more likely than cisgender students
(28% cis women/29% cis men) to do so.
•
Of those who contact a campus program for help, 40% say it
was extremely or very useful and 35% say it was a little or not
at all useful.
STALKING OFFENDERS
•
The majority of college student victims are stalked by someone
they know.
L
o Most stalkers are also students.
o The most common stalkers are former intimate partners
(33%), closely followed by someone the victim knows or
recognizes but is not a friend (31%), then friends (25%),
classmates (18%), and current intimate partners (14%).
•
The most common stalking behaviors reported by college
stalking victims include:
M
o Unwanted voice or text messages (45%).
o Unwanted emails or social media (44%).
o Being approached or seeing the stalker show up at places
when the victim did not want them to be there (37%).
•
Stalkers misuse common technology and use specialized
technology to facilitate stalking:
N
o 24% of college stalking victims have had a stalker create a
fake profile pretending to be the victim.
o 21% have experienced spoofing (calls, texts, or e-mails in
which the stalker makes the contact seem that is coming
from someone else).
o 16% have been doxed (had private or identifying
information published publicly online).
o 16% have been the victim of nonconsensual sharing of
intimate images.
•
People with Autism Spectrum Disorders are more likely to
engage in inappropriate courting behavior and pursue romantic
targets longer,
O
so reports of stalking committed by these
students require specialized interventions that include input
from disability experts.
P
What is stalking?
While legal definitions of
stalking vary from one jurisdiction to another,
Title IX and the Clery Act have a good working
definition of stalking:
Engaging in a course of conduct directed at a specific
person that would cause a reasonable person to (1)
Fear for the person’s safety or the safety of others; or
(2) Suer substantial emotional distress.
?
STALKING AMONG COLLEGE STUDENTS:
FACT SHEET
Stalking is a violation of student conduct codes
and Title IX, and a crime under the laws of the 50
states, District of Columbia, U.S. Territories, and
Federal government.
!
18-24-
y
ear-olds experience the highest
rates o
f
stalking among adults.
K
This makes it vital for colleges to appropriately
address stalking on campus and ensure services
are accessible to all victims.
!
School-Related Impacts for Stalking Victims Include:
• diculty concentrating in class, on assignments,
and during exams
• missing meetings and extra-curricular activities
• dropping classes
• lower grades
• considering dropping out of school
• changing living situation, like moving out of dorms

STALKING VICTIMIZATION
• An estimated 6-7.5 million people are stalked in a one year
period in the United States.
• Nearly 1 in 6 women and 1 in 17 men have experienced stalking
victimization at some point in their lifetime.
• Using a less conservative definition of stalking, which considers
any amount of fear (i.e., a little fearful, somewhat fearful, or
very fearful), 1 in 4 women and 1 in 13 men reported being a
victim of stalking in their lifetime.
• About half of all victims of stalking indicated that they were
stalked before the age of 25.
• Stalkers use many tactics including:
Approaching the victim or showing up in places when the victim
didn’t want them to be there; making unwanted telephone calls;
leaving the victim unwanted messages (text or voice); watching or
following the victim from a distance, or spying on the victim with
a listening device, camera, or GPS.
* Source for the above stats: Smith, S.G., Zhang, X., Basile, K.C., Merrick, M.T., Wang,
J., Kresnow, M., Chen, J. (2018). The National Intimate Partner and Sexual Violence
Survey (NISVS): 2015 Data Brief. Atlanta, GA: National Center for Injury Prevention
and Control, Centers for Disease Control and Prevention.
• The majority of stalking victims are stalked by someone they
know. Many victims are stalked by a current or former intimate
partner, or by an acquaintance.
• People aged 18-24 have the highest rate of stalking victimization.
** Source for the above stats: Catalano, S., Smith, E., Snyder, H. & Rand, M. (2009).
Bureau of Justice Statistics selected findings: Female victims of violence. Retrieved
from http://www.bjs. gov/content/pub/pdf/fvv.pdf.
• Almost half of stalking victims experience at least one unwanted
contact per week.
• 11% of stalking victims have been stalked for 5 years or more.
• 1 in 4 victims report being stalked through the use of some form
of technology (such as e-mail or instant messaging).
• 10% of victims report being monitored with global positioning
systems (GPS), and 8% report being monitored through video
or digital cameras, or listening devices.
*** Source: Katrina Baum et al., “Stalking Victimization in the United States,”
(Washington, DC: Bureau of Justice Statistics, 2009).
IMPACT OF STALKING ON VICTIMS
• 46% of stalking victims fear not knowing what will happen next.
• 29% of stalking victims fear the stalking will never stop.
• 1 in 8 employed stalking victims lose time from work as a result
of their victimization and more than half lose 5 days of work
or more.
• 1 in 7 stalking victims move as a result of their victimization.
**** Source: Katrina Baum et al., “Stalking Victimization in the United States,”
(Washington, DC: Bureau of Justice Statistics, 2009).
• Stalking victims suer much higher rates of depression,
anxiety, insomnia, and social dysfunction than people in the
general population.
****Source: Eric Blauuw et al., “The Toll of Stalking,” Journal of Interpersonal Violence, 17,
no. 1 (2002):50-63.
STALKING OFFENDERS
• 2/3 of stalkers pursue their victims at least once per week, many
daily, using more than one method.
• 78% of stalkers use more than one means of approach.
• Weapons are used to harm or threaten victims in 1 out of 5 cases.
• Almost 1/3 of stalkers have stalked before.
• Intimate partner stalkers frequently approach their targets,
and their behaviors escalate quickly.
****Source: Kris Mohandie et al.,“The RECON Typology of Stalking: Reliability and
Validity Based upon a Large Sample of North American Stalkers,” Journal of Forensic
Sciences, 51, no. 1 (2006).
STALKING LAWS
• Stalking is a crime under the laws of 50 states, the District of
Columbia, the U.S. Territories, and the Federal government.
• Less than 1/3 of states classify stalking as a felony upon first
oense.
• More than 1/2 of states classify stalking as a felony upon second
or subsequent oense or when the crime involves aggravating
factors.
• Aggravating factors may include: possession of a deadly weapon,
violation of a court order or condition of probation/parole, victim
under 16 years, or same victim as prior occasions.
STALKING FACT SHEET
WHAT IS STALKING?
?
While legal definitions of stalking vary from one jurisdiction
to another, a good working definition of stalking is: a course
of conduct directed at a specific person that would cause a
reasonable person to feel fear.
@FollowUsLegally
STALKING PREVENTION, AWARENESS,
AND RESOURCE CENTER
This project was supported by Grant No. 2017-TA-AX-K074 awarded by the Office on Violence Against Women, U.S. Department of Justice. The opinions, findings,
conclusions, and recommendations expressed in this publication/program/exhibition are those of the author(s) and do not necessarily reflect the views of the Department
of Justice, Office on Violence Against Women.
1000 Vermont Ave NW, Suite 1010 | Washington, DC 20005 | (202) 558-0040 | stalkingawareness.org
STALKING AMONG COLLEGE STUDENTS:
FACT SHEET
SOURCES
A
Cantor, D., Fisher, B., Chibnall, S., Madden, K. (2020). Report on the AAU campus climate survey on sexual assault and misconduct. Westat.
Demers, J. M., K. Ward, S., Walsh, W. A., L. Banyard, V., Cohn, E. S., Edwards, K. M., & Moynihan, M. M. (2017). Disclosure on campus: Students’ decisions to tell others about
unwanted sexual experiences, intimate partner violence, and stalking. Journal of Aggression, Maltreatment & Trauma, 27(1), 54-75.
Fedina, L., Backes, B. L., Sulley, C., Wood, L., & Busch-Armendariz, N. (2020). Prevalence and sociodemographic factors associated with stalking victimization among college
students. Journal of American college health, 68(6), 624-630.
B
Brady, P. Q., Nobles, M. R., & Bouard, L. A. (2017). Are college students really at a higher risk for stalking?: Exploring the generalizability of student samples in victimization
research. Journal of criminal justice, 52, 12-21.
Cantor, D., Fisher, B., Chibnall, S., Madden, K. (2020). Report on the AAU campus climate survey on sexual assault and misconduct. Westat.
Fedina, L., Backes, B. L., Sulley, C., Wood, L., & Busch-Armendariz, N. (2020). Prevalence and sociodemographic factors associated with stalking victimization among college
students. Journal of American college health, 68(6), 624-630.
Reyns, B. W., Henson, B., & Fisher, B. S. (2012). Stalking in the twilight zone: Extent of cyberstalking victimization and oending among college students. Deviant Behavior, 33(1),
1-25.
C
Cantor, D., Fisher, B., Chibnall, S., Madden, K. (2020). Report on the AAU campus climate survey on sexual assault and misconduct. Westat.
Reyns, B. W., Henson, B., & Fisher, B. S. (2012). Stalking in the twilight zone: Extent of cyberstalking victimization and oending among college students. Deviant Behavior, 33(1),
1-25.
D
Cantor, D., Fisher, B., Chibnall, S., Madden, K. (2020). Report on the AAU campus climate survey on sexual assault and misconduct. Westat.
Fedina, L., Backes, B. L., Sulley, C., Wood, L., & Busch-Armendariz, N. (2020). Prevalence and sociodemographic factors associated with stalking victimization among college
students. Journal of American college health, 68(6), 624-630.
Reyns, B. W., Henson, B., & Fisher, B. S. (2012). Stalking in the twilight zone: Extent of cyberstalking victimization and oending among college students. Deviant Behavior, 33(1),
1-25.
Reyns, B. W., & Scherer, H. (2019). Disability type and risk of sexual and stalking victimization in a National sample: A lifestyle–routine activity approach. Criminal justice and
behavior, 46(4), 628-647.
E
Reyns, B. W., & Scherer, H. (2018). Stalking victimization among college students: The role of disability within a lifestyle-routine activity framework. Crime & Delinquency, 64(5),
650-673.
F
Elvey, K., Reyns, B. W., & McNeeley, S. (2018). Stalking on campus: A gendered perspective on target congruence and opportunity. Criminal Justice and Behavior, 45, 1308-1327.
G
Brady, P. Q., Nobles, M. R., & Bouard, L. A. (2017). Are college students really at a higher risk for stalking?: Exploring the generalizability of student samples in victimization
research. Journal of criminal justice, 52, 12-21.
Fedina, L., Backes, B. L., Sulley, C., Wood, L., & Busch-Armendariz, N. (2020). Prevalence and sociodemographic factors associated with stalking victimization among college
students. Journal of American college health, 68(6), 624-630.
H
Augustyn, M.B., Rennison, C.M., Pinchevksy, G.M., & Magnuson, A.B. (2019). Intimate Partner Stalking among College Students: Examining Situational Contexts Related to Police
Notification. Journal of Family Violence 35(1), 679-691.
I
Brady. P. Q., & Grin, V. W. (November, 2019). Stalking the next generation: Examining stalking experiences and victim decision-making among Generation Z. Paper presented at
the American Society of Criminology conference in San Francisco, CA.
Brady. P. Q., & Grin, V. W. (March, 2019). Generation iStalk: Tech-facilitated stalking among emerging adults. Paper presented at the Southern Criminal Justice Association
conference in Nashville, Tennessee.
J
Cantor, D., Fisher, B., Chibnall, S., Madden, K. (2020). Report on the AAU campus climate survey on sexual assault and misconduct. Westat.
K
Smith, S.G., Zhang, X., Basile, K.C., Merrick, M.T., Wang, J., Kresnow, M., & Chen, J. (2018). The National Intimate Partner and Sexual Violence Survey (NISVS): 2015 Data Brief.
Atlanta, GA: National Center for Injury Prevention and Control, Centers for Disease Control and Prevention.
L
Cantor, D., Fisher, B., Chibnall, S., Madden, K. (2020). Report on the AAU campus climate survey on sexual assault and misconduct. Westat
M
Fedina, L., Backes, B. L., Sulley, C., Wood, L., & Busch-Armendariz, N. (2020). Prevalence and sociodemographic factors associated with stalking victimization among college
students. Journal of American college health, 68(6), 624-630.
l
N
Brady. P. Q., & Griffin, V. W. (March, 2019). Generation iStalk: Tech-facilitated stalking among emerging adults. Paper presented at the Southern Criminal Justice Association
co
nference in Nashville, Tennessee.
O
Stokes, M., Newton, N., & Kaur, A. (2007). Stalking, and Social and Romantic Functioning Among Adolescents and Adults with Autism Spectrum Disorder. Journal of Autism and
Developmental Disorders, 37(10): 1969-1986.
P
Post, M., Haymes, L., Storey, K., Loughrey, T., & Campbell, C. (2012). Understanding Stalking Behaviors by Individuals with Autism Spectrum Disorders and Recommended
Prevention Strategies for School Settings. Journal of Autism and Developmental Disorders, 44(11): 2698-706.


1
TALKING STALKING:
TIPS FOR PREVENTION/AWARENESS EDUCATORS
Stalking is a serious, prevalent, and dangerous crime that impacts every community in the United States. While
awareness and public discussion of intimate partner violence and sexual assault have increased in recent years, stalking
remains frequently misunderstood and rarely discussed – both within the fields of domestic and sexual violence and
among the broader general public.
It is essential for victims, survivors, service providers, and the criminal justice system to be able to identify and
name stalking. Stalking is a unique crime that calls for particularized safety planning, investigation, charging, and
prosecution, as well as the development and implementation of policies and protocols to ensure an eective response.
For victims, it can be very empowering to accurately name their experiences as “stalking;” it enables them to make
sense of what they are going through and helps them identify and seek appropriate help and resources.
A collective community response is required to end stalking. Friends and family members are usually the first people a
stalking victim talks to about what’s going on and their responses heavily influence whether or not a victim seeks further
help. When friends, family, neighbors, teachers, mentors, and colleagues know how to identify stalking, they are better
able to support victims and help keep them safe.
Dating abuse and/or sexual assault educators have an incredible opportunity to increase knowledge about this commonly
co-occurring crime. With this guide and the referenced materials, SPARC hopes to assist educators in their essential
work to raise awareness of stalking.
THIS GUIDE INCLUDES:
• Strategies to incorporate stalking education into existing SA and DV programming
• Resources for workshops specifically focused on stalking
• Activities, videos, and other resources that can serve as building blocks for your own program
Please reach out to the Stalking Prevention, Awareness & Resource Center ([email protected])
with any questions or for additional assistance.
INTRODUCTION – WHY NAME STALKING?

2
NAME/IDENTIFY STALKING.
Stalking is generally defined as a pattern of behavior targeted at a specific person that would cause a reasonable
person to feel fear. Fear is central to the definition of stalking. Common stalking behaviors include (but are not
limited to) following, repeated contact, surveillance, spreading rumors, and threats.
RECOGNIZE THAT STALKING OFTEN CO-OCCURS WITH THE ISSUES YOU’RE ALREADY
EDUCATING ON.
Consider the behaviors and examples that you already use in your workshops to illustrate interpersonal violence – it’s
very likely that you’re already talking about stalking! Simply explaining that “X behavior is also an example of stalking,
a prevalent crime that may co-occur with dating violence/sexual assault” can be a major step in helping victims identify
their experiences and seek more information. More specific suggestions are below.
If your organization provides information on sexual assault, intimate partner violence, harassment in the workplace,
elder abuse, child abuse, and/or a variety of other issues, stalking is relevant to your topic. Adding some statistics and/
or examples about the intersection of stalking with your main topic can be an easy and time-ecient way to incorporate
stalking into your educational eorts.
PROVIDE RESOURCES, EXAMPLES, AND VICTIM/SURVIVOR STORIES.
Consider the information and materials that you disseminate during presentations, on social media, and/or your website.
Is information about stalking included? Do you define what it is? When providing case scenarios, do you ensure that your
examples feature stalking? Do you link to Victim Connect or to local resources that address stalking? Make stalking
part of the conversation.
WHAT IS STALKING?

3
While you do not have to be an expert on stalking, educators should have basic knowledge about the definition,
dynamics, and prevalence of stalking. Please consider reviewing the following resources:
• Stalking: Definition and FAQs
• Stalking Fact Sheet
• Webinar – Stalking: Know It, Name It, Stop it
• Understanding Stalking Brochure
Many educators are given limited time to present on a variety of substantive and complex topics. If you
are not able to dedicate an entire program to the topic of stalking, please consider the following ways to
incorporate stalking into existing training.
UNDERSTANDING STALKING
INCORPORATING STALKING INTO EXISTING
DV AND SV PROGRAMMING
ADD ONE SLIDE ON STALKING.
If possible, add one slide with very basic information
on stalking. Sample below (and available for download
here).
IDENTIFY STALKING WHEN EDUCATING ON
RELEVANT ABUSIVE BEHAVIORS.
Many behaviors that are often described as “emotional
abuse,” including (but not limited to) texting or calling
constantly, surveillance, tracking using technology,
demanding constant check-ins, asking friends/family/
colleagues where the victim is and following, are also
examples of stalking behavior. In a presentation on
dating abuse or domestic violence, simply identifying
these behaviors as stalking can easily convey that
stalking is a distinct crime and form of victimization.

4
SAMPLE SPEAKING NOTES ON STALKING
(Best Practice: Speak about stalking after emotional abuse)
• Many emotionally abusive behaviors can also be categorized as stalking.
• Stalking is a crime.
• Stalking can happen in a relationship as a type of emotional abuse, or it can happen outside a romantic relationship.
The stalker could be a partner, friend, neighbor, or even a stranger.
• Stalking is scary and often becomes dangerous.
• If you’re experiencing stalking, you may want to seek help (provide resources).
• Specifically identify stalking in your case studies, survivor stories, and examples. Is there a story/case study that
you use in your trainings? Does it involve stalking? If so, articulate it. Simply saying “the oender also stalked the
victim – [list of behaviors] – and it’s important to realize that stalking can be a dangerous predictor of violence and
even murder” can be powerful.
Analyze the examples that you use for any identifiable stalking behaviors and highlight them as such.
INCORPORATE STALKING EXAMPLES INTO BYSTANDER INTERVENTION EDUCATION.
Bystander intervention education can and should include examples of stalking, particularly when discussing cultural
change/social norms. Just as learners are encouraged to be active bystanders who say something when they witness
peers being abusive, they can “call out” stalking behaviors as well and try to change the norms. For example: “Hey,
stop asking her roommate where she is – she’ll text you if she wants to” or “It’s not right to look through his phone
like that.” These can be incorporated in trainings as well as public awareness campaigns.
There are limitations to including stalking in bystander intervention education. Stalking is a pattern of behaviors,
so the incident-based intervention scenarios campuses often use for sexual assault (i.e., “You notice an upperclassman
plying a freshman with drinks at a party”) are typically not quite as relevant. Bystanders could be encouraged to step
in if they witness an act of stalking, but should also recognize they are probably only impacting one act in a pattern
of behavior.
For instance, campus educators often tell the dating abuse story of Yeardley Love, a lacrosse player at the
University of Virginia who was murdered by her abusive ex-boyfriend (George Huguely) in 2012. This is an
opportunity to educate on stalking, as the perpetrator also engaged in stalking behavior including (but not limited
to) sending threatening e-mails and following her.

5
COMPLETE SCRIPTED CURRICULA AT
STALKINGAWARENESS.ORG
SPARC has two complete stalking public awareness
trainings with slides and speaking notes free and available
for download on the website. One is designed to inform
the general public, and the other is for professionals in the
DV field. The recommended time needed for both
of these presentations is one hour.
Materials are free to down load, edit and utilize, simply
credit SPARC. Please include this citation: These ma-
terials are provided courtesy of the Stalking Prevention,
Awareness & Resource Center (SPARC) of AEquitas,
funded by the DOJ Oce of Violence Against Women.
UNDERSTANDING STALKING THROUGH
MEDIA
Using media can be an engaging way to encourage
participants to think critically about an issue and the
myths surrounding it. In popular media, stalking is often
shown as romantic, harmless, and/or funny. There are
many problematic media portrayals of stalking worth
analyzing.
Stalking is a complex and important topic, and participants can benefit from longer trainings
that focus on stalking specifically. Activity-based sessions should be contextualized with some
basic information on stalking. Consider this short lesson (10 simple slides total with speaking
notes) on stalking to frame your activity/activities.
LEADING A SEPARATE WORKSHOP
OR TRAINING ON STALKING
Resources on popular media and stalking:
• These slides from SPARC (with speaking notes)
highlight some of the impacts of media
normalization of stalking. These can be used to help
build your session.
• Discussion questions for the Lifetime/Netflix
series You.
The popular Lifetime/Netflix show You focuses on
intimate partner stalking. Consider facilitating a
conversation around these questions.
• Pop Culture Detective: Stalking for Love
This video highlights and analyzes the trope of
stalking as a form of love.
• Trailers and clips from music videos, film and TV.
From cartoons to romantic comedies to superhero
films, there are many examples of stalking in media.
Typically, the stalking behavior is framed as harm-
less, funny, cute or romantic – it is almost never
named or explored for the dangerous crime it really
is. Brainstorm some examples in your community or
reach out to SPARC for suggested examples.

6
Short Videos with victim and survivor stories are another
powerful way to educate on stalking. You could build
a short program or discussion around a video for a
stand-alone presentation or incorporate the video into an
existing workshop. To the right are a few video clips to
consider.
To best meet the needs of your community, you may want
to search for stalking case examples on your own that
reflect your location and/or population (i.e.,
college campuses). Reach out to SPARC if you are
seeking examples.
Real Fear, Real Crime: The Peggy Klinke Story
Produced by the Stalking Resource Center and Lifetime
Television, this 18-minute training video was created in
response to the murder of stalking victim Peggy Klinke by
a former partner.
Stalking Videos and Discussion Guides
from OutrageUs.org
Designed with the domestic violence field in mind, this
7-part mini docuseries (with videos ranging from
2 – 8 minutes) features survivors, law enforcement, and
victim advocates discussing the dynamics and impacts
of intimate partner stalking as well as tools to fight back.
Each video has a discussion guide.
Including a participatory activity or two in a stalking workshop
can help engage your audience and reduce the amount of lecture to prepare.
Sample Activity with Behavior Cards
(Note: This activity should be used along with slides
defining stalking and providing more information.)
In pairs or small groups, choose up to 5 cards, one at
a time. Consider each card as part of a pattern of
behavior/course of conduct from the same victim.
After each card you select, discuss the following
questions as a group:
1. How would you feel if this happened to you or to a
friend? Scared? Confused? Flattered? Annoyed?
2. Does this seem like a stalking case?
3. Is this potentially criminal behavior? Why or why not?
4. What are some ways that you could plan for safety?
1. Stalking Behavior Cards
These cards can be adapted for your
audience, printed, cut out, and used
for a variety of activities.
ADDITIONAL RESOURCES FOR DEVELOPING TRAININGS
ON STALKING PROGRAM
ACTIVITY IDEAS

7
2. Stalking Behavior Brainstorm
Stalkers engage in a variety of behaviors to scare
their victims. Ask participants to brainstorm stalking
behaviors that could be considered under one of the
categories listed to the right, then ask participants to
share what they discussed. These categories are from
Stalking: A Multidimensional Framework for
Assessment and Safety Planning.
Surveillance Life Invasion Interference Intimidation
List examples of Provide examples How is the stalker In what ways is
how the stalker of how the stalker interfering in the stalker
acts to watch, “shows up” and the victim’s life? threatening
track, and/or invades the victim’s What is the victim the victim?
monitor the victim. invades the victim’s losing or afraid to
victim does not lose as a result of
want the stalker to the stalker’s behavior?
be there.
Give participants drawing materials (ideally, large pieces of flipchart paper and writing implements) and a time limit.
You may wish to hang paper around the room with these three dierent questions so that attendees move from one
chart to another.
In small groups, ask them to draw or write answers to the following questions from a victim’s perspective and/or from
an outsider’s (like a friend) perspective:
1) What does stalking look like?
2) What does stalking sound like?
3) What does stalking feel like?
Have participants report out. Highlight the diverse ways that victims may experience stalking and the contextual
nature of stalking, noting the following points:
• Stalking behaviors often have specific meanings between stalkers and their victims.
For example, a stalker might say “I’ll send you roses the day I kill you.” When the victim receives the roses,
the victim is terrified. Outsiders might remark how nice it is that they received roses. Alternatively, stalkers
may be overtly threatening or violent.
• Fear is essential to the definition of stalking.
Many stalking victims feel scared, trapped, and like they are always looking over their shoulder.
3. How Does Stalking Look? Sound? Feel?
ACTIVITY IDEAS

8
4. Romantic Pursuit? Bullying/Cliques? Stalking?
Stalking is a highly contextual crime. Hang signs on dierent walls in the room:
“Romantic Pursuit,” “Bullying/Cliques,” and “Stalking.” Read the following behaviors out loud and ask participants to
choose under which heading the behavior belongs.
SAMPLE BEHAVIORS (note that these examples were written with a campus audience in mind.
Feel free to adapt or add any that are relevant to your audience):
The person…
1) Unexpectedly (and repeatedly) approaches you o campus: at the movies, out to coee with your friends,
at a party.
2) Brings flowers to every a cappella concert that you’re in, leaves “good luck” and “congratulations” notes on
your dorm room door.
3) Takes your phone and reads your texts, emails, and incoming chats.
4) Steals things like your textbooks and jacket so that you have to go ask for them back.
5) Transfers classes to be in yours.
6) Sends multiple texts a day to check in, regardless of whether or not you respond.
7) Finds embarrassing information about you online and shares it with others.
8) Watches where you go – in the cafeteria, between classes, in the library.
9) Hacks into your Instagram account and pretends to be you.
10) Tries to be friends with your friends and roommates without invitation.
Ask a few attendees to explain their responses to the larger group, then facilitate a discussion highlighting the contextual
nature of stalking. The take-home point is to recognize that some of these may be stalking behaviors – particularly if
they are scary, become a pattern and/or seem to be escalating. Since stalking is a pattern of behaviors that can escalate
over time, sometimes fear doesn’t attach until later and the first behavior(s) might seem innocent or easy to excuse.
Participants should be encouraged to trust their instincts and think about at what point they would (or wouldn’t)
consider this a stalking pattern of behavior as the example behaviors increase.
Thank you for incorporating stalking into your essential education work. Do not hesitate to reach out to SPARC (info@
stalkingawareness.org) for more guidance, feedback on curricula, suggestions for cases or media examples or to share
the work that you’re doing to raise awareness on stalking.
This project was supported by Grant No. 2017-TA-AX-K074 awarded by the Oce on Violence Against Women, U.S. Department of Justice. The opinions, findings, conclusions, and
recommendations expressed in this program are those of the author(s) and do not necessarily reflect the views of the Department of Justice, Oce on Violence Against Women.
ACTIVITY IDEAS

•
•
•
•

➢
➢

•
•
•
•
•
•
•
•
•
•
•
•
•
•
•
•
•
•
•
•

Stalking is a serious, prevalent, and dangerous crime that impacts every campus in the United States; that is a violation of
student conduct codes and Title IX; and that is a crime under the laws of the 50 states, District of Columbia, U.S. Territories,
Uniform Code of Military Justice, and Federal government, as well as many tribal jurisdictions.
When a school investigates a report of stalking and holds disciplinary or Title IX hearings, there are a lot of things to consider.
This document provides guidance on what is important to consider and what is important to ask the victim/complainant and
accused stalker/respondent. To refresh your understanding of stalking, watch webinars and read resources at
StalkingAwareness.org. To review how stalking is covered under Title IX, see our resource on The Basics of Stalking and Title IX
.
Schools that receive federal funding are required by Title IX to remedy any
situation of sex discrimination, address its effects, and prevent it from
happening again. Violating these requirements could cause a school to lose
its federal funding or be liable for monetary damages to the student whose
rights were violated.
IMPORTANT CONSIDERATIONS
Victims’ perceptions of their own risk and what their stalker is capable of
are one of the most accurate predictors of risk. The Stalking and
Harassment Assessment and Risk Profile (SHARP) is a tool designed
specifically to examine and assess stalking. It is a free web-based
assessment available at www.CoerciveControl.org
that assesses the “big
picture” of the stalking situation and a victim’s risk in the moment.
Remember that victims are sometimes unsure if what they are
experiencing violates student conduct codes, Title IX, or criminal statutes.
In fact, 43% of college stalking victims who meet the legal criteria of stalking do not identify their experience as “stalking.”
i
And
while 92% of college stalking victims tell friends and/or family about the unwanted pursuit behaviors, only 29% contact a
program or resource for help.
ii
So, your contact is critical! Your response may determine how or if the victim continues to get
help or participates in the investigation and hearing process.
When first meeting with a victim, make sure to:
• Have stalking resources on hand, like brochures about stalking and available campus and local support services.
• Discuss the possibility of recording an audio or video victim statement to preserve what the victim says along with their
demeanor and explain why that would be helpful.
• Discuss the options of engaging with the criminal legal system and how an audio or video victim statement would be
helpful in that situation.
• Preserve evidence immediately, for example taking pictures of text messages.
• Prepare for the long haul. Stalking investigations are often long, resource-intensive investigations.
• Conduct a thorough interview and gather information now. This ensures other responders down the road can do their
jobs well, too.
Title IX defines stalking as a pattern of
behavior directed at a specific person that
would cause a reasonable person to fear for
the person’s safety or the safety of others;
or suffer substantial emotional distress.
The individual incidents that establish a
pattern of behavior may not be a violation
on their own.
Fear is central to the definition of stalking.
Common stalking behaviors include—but
are not limited to—repeated unwanted
phone calls and messages, showing up when
uninvited, following, surveillance, spreading
rumors, and threats.

Victims are often the first to minimize what is happening to them and friends, family, peers, and responders also often
downplay the seriousness. Any time a victim reports any type of harassing behavior, consider the possibility of a stalking case
and determine whether it is an isolated incident or repeated conduct. Overall, remember to:
• Look at the duration, intensity, and frequency of the behavior.
• Focus on respondent behavior.
• Consider what the victim has changed in their life in response to the behavior.
• Explain to the victim what their reporting options are and respect their decision; community advocates and criminal
legal professionals may be better positioned and resourced to help.
Listen closely and document everything a victim reports, even if what they say sounds unbelievable. It’s important to ask open-
ended questions and give the victim plenty of time to respond. It is also important to recognize the impact trauma has on victim
responses. In general, you want to ask questions about the context of the situation, the type of repeated and unwanted contact
that happened, and how it interfered with their life and/or made them feel fearful. It’s often helpful to explain to the victim why
you are asking a question and its context as part of the legal definition of stalking. When discussing any technology-facilitated
stalking, it’s important to explain that law enforcement may be better able to seize and examine any electronic evidence.
Do you know the stalker?
o How long have you known them?
o How would you describe your relationship?
o Has your relationship changed?
o How has your relationship changed?
o What type of contact was typical in your
relationship? (medium and frequency)
Was there something in particular that made you
decide to come in today?
What do you remember about the timeline or history
of this contact?
How did you receive the contact? (Phone call, email,
social media platform/app, text, etc.)
If it was electronic, how did you identify the sender?
People react to situations like this in a variety of ways,
and there’s no “right” or “wrong” way; it’s important for
us to document how the contact made you feel, so are
you able to describe in your own words what your
response was?
Would you explain in your own words why the contact
made you feel that way?
What did you think might happen to you as a result of
the contact?
Did you keep any records of what was happening, like a
documentation log?
People react to situations like this in a variety of ways,
some continue communication and some do not; what
type of communications have you had with the stalker
or have you stopped communicating with them?
Do you believe the stalker knows that you do not want
any more communication? Why do you believe that?
Has the contact increased, decreased, ceased?
Did every contact scare you, or at what point did you
become frightened?
Are you able to tell me about any impact this has had
on your daily life? If so, how?
Did you change your routines or activities as a result of
what has occurred?
Has there been any impact on your academics and/or
job that you’re able to tell me about?
Have you done anything differently in your life as a
result of this situation?
Have you gotten new phone numbers, email accounts,
social media accounts, etc. and not told the person
contacting you?
Has anyone witnessed any of the events that have
happened?
QUESTIONS TO ASK THE VICTIM / COMPLAINANT

This project was supported by Grant No. 2017-TA-AX-K074 awarded by the Office on Violence Against Women, U.S. Department of Justice. The opinions, findings,
conclusions, and recommendations expressed in this publication/program/exhibition are those of the author(s) and do not necessarily reflect the views of the Department
of Justice, Office on Violence Against Women.
@FollowUsLegally
The
importance of protecting fairness and due process rights for all students is a recognized goal of Title IX regulations.
Communicating to the accused/respondent that they don't have to answer questions and that they are free to leave an
interview can, at a minimum, demonstrate a statement is voluntary. It’s important to ask open-ended questions and give the
accused/respondent plenty of time to respond. In general, you want to learn whether the respondent knew or should have
known that the contact was unwanted. Many respondents express that the situation is a misunderstanding, so it’s often helpful
to ask, “how is what you’re doing being misunderstood?” to learn what they think about their behavior. Discuss the possibility of
recording an audio or video statement to preserve what the accused/respondent says along with their demeanor, which is often
very helpful in the investigation and hearing process.
Do you know the complainant?
o How long have you known them?
o How would you describe your relationship?
o Has your relationship changed?
o How has your relationship changed?
o What type of contact was typical in your
relationship? (medium and frequency)
Who are people familiar with the relationship between
you and the complainant?
Describe your contact with the complainant.
Describe the timeline or history of this contact.
How did you contact them?
Did you receive a response? What was it?
What was the purpose of the contact?
Why did you continue the contact (either after you
were asked to cease, when responses ceased, or when
no response was received)?
What electronic communication devices do you use?
What is your cell phone provider?
What social media accounts do you use and what are
your user names?
What devices do you use to access social media?
What is your internet service provider?
Where and how do you access the internet?
Have you ever been accused of something like this
before?
o By whom?
o When?
If you
learn of other incidents or behavior that may violate Title IX or be criminal behavior—like sexual assault, strangulation,
vandalism, burglary, trespassing, or nonconsensual distribution of intimate images—make sure to document the incident(s),
discuss reporting options with the victim, and follow your own reporting requirements.
Please contact the Stalking Prevention, Awareness, & Resource Center (info@stalkingawareness.org
) with any questions or
for additional assistance to support victims and hold stalkers accountable.
i
Brady, P. Q. & Woodward Griffin, V. (2019). The Intersection of Stalking and Sexual Assault Among Emerging Adults: Unpublished Preliminary Results, mTurk Findings, 2018.
ii
Cantor, D., Fisher, B., Chibnall, S., Madden, K. (2020). Report on the AAU campus climate survey on sexual assault and misconduct. Westat.
QUESTIONS TO ASK THE ACCUSED / RESPONDENT
FOLLOW-UP
1000 Vermont Avenue NW, Suit
e 1010 | Washington, DC 20005 | (202) 558-0040 | stalkingawareness.org

1
This bench card is designed for use in conjunction with the more comprehensive
Judicial Officer Guide for Responding to
Stalking and as a reference when considering the role of stalking in Federal courts; Tribal courts; immigration courts; state
family, juvenile, civil, and criminal court cases; and administrative law adjudications including immigration and Equal
Employment Opportunity Commission adjudications. Judicial officers are strongly encouraged to read
the full Guide prior to
using this bench card during proceedings.
This bench card serves as a reference for judicial officers on stalking behaviors and how these behaviors relate to other crimes,
to be better able to identify stalking in any type of case. Judicial officers are encouraged to make specific findings of fact
regarding stalking and issue detailed orders designed to stop stalking behaviors, hold offenders accountable, and prevent
dangerous consequences.
CONSIDERING/IDENTIFYING STALKING
Stalking can appear in any type of case and it is particularly important to look for indicators when the parties
know one another and/or there is evidence of ongoing harmful contact. Stalking can occur in the context of
other crimes and other crimes can occur in the context of stalking.
Stalking should be considered in protection order and domestic violence hearings
because intimate partner
stalkers are more likely (than stalkers with other relationships to their victims) to physically approach the
victim; be interfering, insulting, and threatening; use weapons; escalate behaviors quickly; and re-offend.
Technology-facilitated stalking (cyber-stalking) needs particular consideration and concern in stalking cases.
Perpetrators of stalking use and misuse technology to facilitate their stalking. They use computers, social
media, mobile phones, and other devices in their stalking behaviors to monitor, contact, control, and isolate
their victims, as well as to damage their victims’ credibility or reputation. The impact of technology-facilitated
stalking is vast and may be just as threatening and fear-inducing as in-person stalking. Victims of technology-
facilitated stalking often report higher levels of fear than individuals who experience in-person stalking
i
ASSESSING STALKING
It is extremely important to note that victims of stalking often do not identify their victimization as stalking or harassment and
are unlikely to use those words to describe what they’re experiencing; instead, they often describe the stalking behaviors and
impacts.
ii
As such, it is important to use a framework for assessing the presence of stalking rather than rely on victims to
identify and name it. Stalkers often try to argue that their behavior is based on a legitimate purpose (to see the kids, to share
the car, to drive down the street, etc.), is a coincidence, or is not itself criminal behavior; however, if their behavior is a pattern
that shows the intent to survey, invade, intimidate, or interfere with/sabotage the victim using the behavior, then their actions
legally meet the evidence-based definition of stalking. Stalking can be done in-person, using technology, or both.
2
SLII STALKING TACTICS
Dr. TK Logan's multi-dimensional framework, focused on Surveillance, Life Invasion, Intimidation, and Interference through
sabotage or attack (SLII) tactics, provides a research-informed approach to assessing stalking behaviors in judicial
proceedings.
iii
The examples of SLII tactics below pertain to all types of victim-stalker relationships.
Follow, watch, monitor, wait for, show up uninvited, track using
software or devices, gather information, proxy stalking (using a
third party to stalk and report on the victim)
Unwanted/nonconsensual contact and communication,
show up without warning, property invasion, public
humiliation, harass friends/family
Explicit and implicit threats, property damage, symbolic
violence, forced confrontations, threat to or actually harm self,
threat to harm others, deportation threats
Financial and/or work sabotage, ruin reputation, custody
interference, keep victim from leaving, road rage, attack
friends/family/children/pets, physical or sexual attack
DURATION, INTENSITY, FREQUENCY
The framework also explains that stalkers use SLII tactics in a dynamic way that can be measured by the Duration, Intensity, and
Frequency of implementation.
•
Duration
is how long the tactics have gone on — when the stalking started and how long it has lasted.
•
Intensity
is the number of different tactics and locations that the stalker employs.
•
Frequency
is how often the stalker makes their presence known — how often the stalker approaches, confronts, and/or
interferes in the victim’s life.
Whether the offender exhibits one continuous tactic or a variety of tactics, the longer the duration and greater the intensity
and frequency of any stalking tactics, the greater the risk of harm, persistence, escalation, and life sabotage
.
iv
Data show
greater victim psychological distress in response to greater frequency of stalking and to any changes in stalker behavior, and
escalation is known to lead to greater violence.
v
ESTABLISHING FEAR
In the vast majority of stalking situations, the stalker knows
their victim
vi
and so may have unique and intimate
knowledge about their victim’s vulnerabilities and what
would scare them. Stalking behaviors often include a
specific meaning only understood by the victim, and may
be intended to seem benign to anyone other than the
victim. When the offender targets a victim with specific
incidents or tactics that the victim finds frightening, this
may show the offender’s intent to frighten them.
Victims react to stalkers in a variety of ways, and fear is
often masked by other emotions: anger, frustration,
hopelessness, despair, or apathy. Some may minimize and
dismiss their stalking as “no big deal.”
3%
6%
20%
9%
44%
32%
4%
9%
19%
8%
41%
43%
Person of Authority
Family Member
Stranger
Brief Encounter
Acquaintance
Current/Former
Intimate Partner
Stalking Victim & Offender Relationships
vi
Female Victims
Male Victims
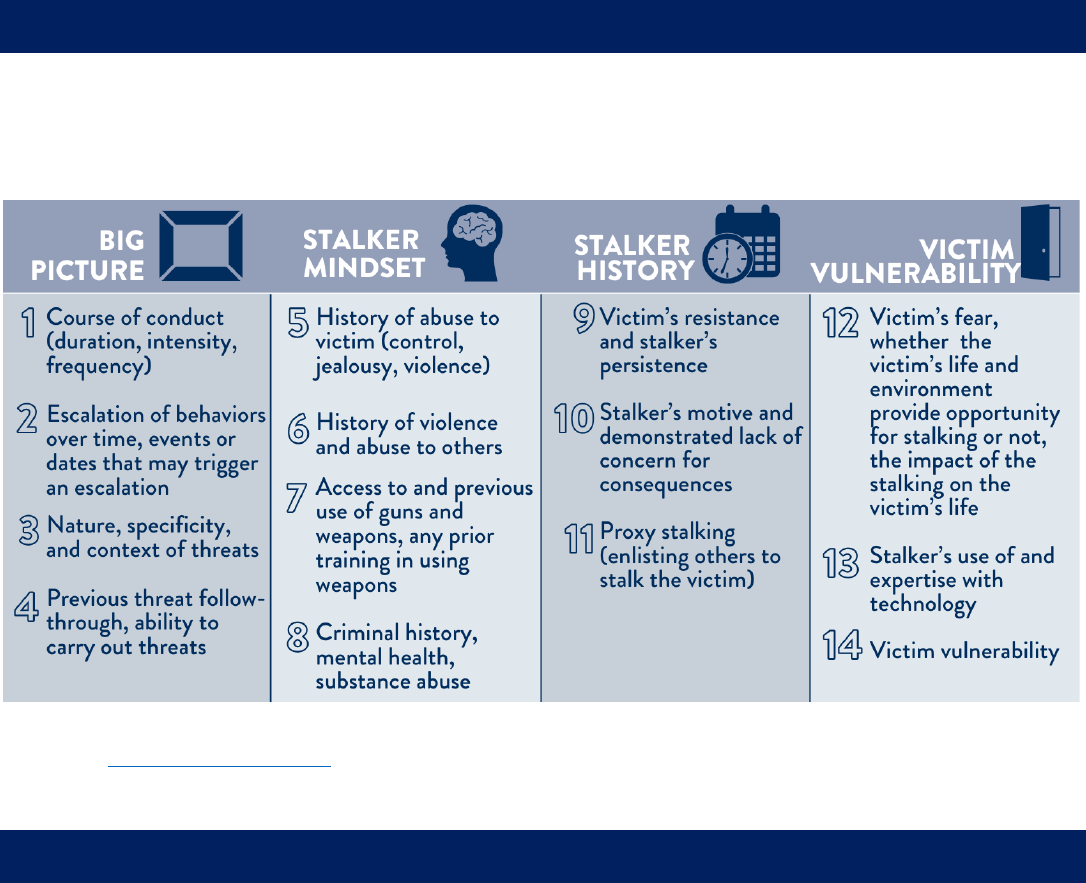
3
It is helpful to consider how victims change their behaviors to cope with the stalking. At a minimum, these are signs that the
stalker’s behaviors are unwanted and the victim is resisting the contact. Evidence and corroboration of the victim’s fear and
resistance can be found by considering changes and accommodations the victim has made to their life.
Some victims continue to have contact and engage with the stalker as a safety strategy, to gather information, assess the
offender’s state of mind, and negotiate their safety. Contact on the part of the victim does not mean that the victim is not in
fear or that the stalker’s behaviors are wanted. In fact, it may indicate that the victim is very afraid of the offender and is
contacting the offender to be able to assess and plan the steps they will take to increase safety for themselves and others.
RISK FACTORS
When reviewing a stalking case, there are 14 factors to consider in assessing the risk posed to victims. Evidence-based research
has found that the presence of or increase in any of the factors contributes to increased risk of current and future harm to the
stalking victim.
vii
(Note that there may be additional risk factors unique to a case that do not fit neatly into one of these
categories but that should still be considered.)
The Stalking and Harassment Assessment and Risk Profile (SHARP) is a web-based tool that provides a situational risk profile
(available at www.CoerciveControl.org
). This risk assessment is useful for several considerations: pretrial detention and bail
conditions, which cases may demand greater attention, and sentencing and post-sentencing (e.g., probation or parole).
COURT ORDERS AND FINDINGS
• Courts can specifically design court orders containing no-contact provisions, mitigating direct contact between the
victim and offender, and utilizing other available safety measures. Providing qualified interpreters in proceedings involving
stalking and translating court orders when the offender and/or the victim are limited English proficient promotes offender
compliance and victim safety.
• Identifying and distinguishing stalking from other forms of intimate partner violence occurring in a case enhances the
effectiveness of court orders in protection order and domestic violence related custody and divorce cases. Victims cannot
violate their own protection orders because the orders circumscribe only the offender’s behavior, not the victim’s.
• Detailed findings regarding the stalking behaviors and their frequency, duration, and intensity also help appraise future
judicial officers who hear actions involving the same parties of the severity of the abuse occurring in the case.

4
PROTECTION ORDERS & BAIL CONDITIONS
Consider orally informing the offender of conditions and prohibitions for protection orders and bail in court (particularly the
prohibition from possessing firearms, ammunition, and related permits and their associated verifiable surrender), as well as that
violations can result in revocations of bail, probation, etc. and may be the basis for (additional) criminal charges. Use qualified
interpreters in any criminal, family, or civil case involving people with limited English proficiency. Having court orders translated
into the languages spoken by the offender and/or victim promotes greater compliance and victim safety.
When stalking behaviors are present, both protection orders and bail conditions should:
Include no-contact provisions that carefully specify prohibitions on indirect as well as direct contact, including
contact through the use of technology and social media, and any other conditions (e.g., GPS monitoring or
restrictions on use of digital devices) that will help to ensure the victim’s safety.
Specify that “no contact” includes indirect contact and contact through third parties, as well as social media
posts about, or directed toward, the victim.
Prohibit contact with members of the victim’s family or household and, in appropriate cases, the victim’s
employer and named friends of the victim.
Prohibit the offender from monitoring, tracking, or surveilling the victim, by use of technology or otherwise.
List any locations frequented by the victim and specify the distance that the stalking perpetrator must stay away from
these locations.
Address when the offender and victim regularly frequent the same places (e.g., a church or a gym) — the order should
bar the offender from those locations completely except during times specified in the court order (designing the order
so that the victim is safe to be at the location except during the hours that the offender is authorized to be there).
Specify that if the offender arrives at a public location and the victim is present, the offender must promptly depart.
Prohibit the offender from possessing firearms, ammunition, and firearms permits; require verifiable surrender of
any of these that the offender currently possesses, and orally inform the offender of this prohibition in court.
Require the Prosecuting Attorney in a criminal case be informed of any attempt made by the Defendant to
purchase a weapon that is rejected by a Federal database.
Require electronic monitoring of the offender (e.g., ankle bracelet) and regular in-person reporting to probation.
Prohibit the use of alcohol or recreational drugs.
EXAMPLE OF STALKING FINDINGS
Petitioner, name, is a victim of stalking. Respondent, name, has utilized [insert stalking tactics categories, i.e., Surveillance, Life
Invasion, Intimidation, Interference through sabotage or attack] through the following behaviors [list the behaviors that fall
under the respective category]. These behaviors are found to be stalking tactics. Respondent, name, has executed these
behaviors that display a pattern of stalking [name the pattern; include frequency, duration, and intensity]. Respondent’s pattern
of behavior escalated and resulted in greater threat and/or violence against Petitioner, name. Respondent’s actions constitute
stalking [insert citation to state law definition]. HAVING MADE THESE FINDINGS… [Insert detailed specific orders to stop
that specific behavior].

5
ENDNOTES
i
Fissel, E. R., & Reyns, B. W. (2020). The Aftermath of Cyberstalking: School, Work, Social, and Health Costs of Victimization. American Journal of Criminal Justice, 45(1),
70-87.
ii
Jordan, C. E., Wilcox, P., & Pritchard, A. J. (2007). Stalking acknowledgement and reporting among college women experiencing intrusive behaviors:
Implications for the emergence of a “classic stalking case”. Journal of Criminal Justice, 35(5), 556-569.
iii
Logan, TK & Walker, R. (2017). Stalking: A Multi-dimensional Framework for Assessment and Safety Planning. Trauma, Violence and Abuse, 18(2), 200-
222.
iv
Id.
v
Id.
vi
Smith, S.G., Basile, K.C., & Kresnow, M. (2022). The National Intimate Partner and Sexual Violence Survey (NISVS): 2016/2017 Report on Stalking.
Atlanta, GA: National Center for Injury Prevention and Control, Centers for Disease Control and Prevention.
vii
Logan, TK & Walker, R. (2017). Stalking: A Multi-dimensional Framework for Assessment and Safety Planning. Trauma, Violence and Abuse, 18(2), 200-
222.
Learn more at StalkingAwareness.org
This project was supported by Grant No. 2017-TA-AX-K074 awarded by the Office on Violence Against Women, U.S. Department of Justice. The
opinions, findings, conclusions, and recommendations expressed in this publication/program/exhibition are those of the author(s) and do not
necessarily reflect the views of the Department of Justice, Office on Violence Against Women.

Judicial Officer Guide: Responding to Stalking Page 1
St
alking Prevention, Awareness, and Resource Center (SPARC)
1000 Vermont Avenue NW, Suite 1010 | Washington, DC 20005 | (202) 558-0040 | info@stalkingawareness.org
www.StalkingAwareness.org
National Council of Juvenile and Family Court Judges
P.O. Box 8970 | Reno, NV 89507 | (775) 507-4777 | [email protected]
www.ncjfcj.org
Nat
ional Immigrant Women’s Advocacy Project (NIWAP)
American University, Washington College of Law
4300 Nebraska Avenue NW N100B | Washington, DC 20016 | (202) 274-4457 | niwap@wcl.american.edu
www.wcl.american.edu/impact/initiatives-programs/niwap
Th
is project is a collaboration between the Stalking Prevention, Awareness, and Resource Center (Julia Holtemeyer and Jennifer Landhuis)
and the National
Immigrant Women’s Advocacy Project, American University, Washington College of Law (Corrin Chow and Leslye E. Orloff). This project was supported by Grant
No. 2017-TA-AX-K074 awarded by the Office on Violence Against Women, U.S. Department of Justice. The opinions, findings, conclusions, and recommendations
expressed in this publication/program/exhibition are those of the author(s) and do not necessarily reflect the views of the Department of Justice, Office on Violence
Against Women.
Table of Contents
I. Introduction ............................................................................................................................................... 3
A. Why Focus on Stalking? ................................................................................................................. 3
B. Stalking Relationships & Dynamics ............................................................................................... 4
C. Stalking in Other Crimes & Cases ................................................................................................ 4
II. Understanding Stalking ............................................................................................................................ 5
A. Framework for Understanding Stalking ......................................................................................... 7
B. Components of Stalking: Intentional Course of Conduct ......................................................... 7
i. SLII Stalking Tactics: Surveillance, Life Invasion, Intimidation, and Interference through
sabotage and attack .................................................................................................................. 8
ii. Stalking Perpetration: Duration, Intensity, Frequency ....................................................... 9
iii. Applying an Understanding of Stalking Tactics and Perpetration in Court Cases .......... 9
C. Components of Stalking: Reasonable Fear ................................................................................. 11
D. Components of Stalking: Unwantedness ................................................................................... 12
E. Technology-Facilitated Stalking ................................................................................................... 13
III. Assessing Risk in Stalking Cases ........................................................................................................... 14
IV. Co-Occurring and Interconnected Crimes ........................................................................................ 15
A. Stalking & Intimate Partner Violence .......................................................................................... 15
B. Stalking & Human Trafficking ....................................................................................................... 16
C. Stalking & Witness Intimidation .................................................................................................... 17
D. Stalking & Sexual Violence ............................................................................................................ 17
E. Stalking & Protection Order Violations ....................................................................................... 18
V. Stalking, Coercive Control, and Battery or Extreme Cruelty........................................................... 19
VI. Capturing Stalking Tactics in Rulings ................................................................................................... 21
A. Example of Stalking Findings ....................................................................................................... 24
B. Example of Coercive Control Findings ....................................................................................... 24
VII. For More Information ............................................................................................................................ 24
Appendix A: Judicial Officer Bench Card ................................................................................................... 28

Judicial Officer Guide: Responding to Stalking Page 3
I. INTRODUCTION
This Judicial Guide is designed to work in conjunction with federal, state, Tribal, and territorial stalking
laws. Judicial officers should consider stalking in all types of legal proceedings, including in Federal
courts; Tribal courts; immigration courts; state family, juvenile, civil, and criminal court cases; and
administrative law adjudications including immigration and Equal Employment Opportunity
Commission adjudications. Since the first stalking statute was passed in 1990, stalking had been
codified as a crime in the 50 states, District of Columbia, Federal
Government, U.S. territories, Military Code, and many Tribal Codes.
i
Judicial officers can use this tool to:
• Help identify the patterns and behaviors of stalking;
• Provide courts the background needed to readily identify stalking patterns and behaviors; and
• Include findings regarding stalking, using model judicial order language, in court orders.
A. WHY FOCUS ON STALKING?
Stalking is a crime that warrants special attention by courts because victims report experiencing
stalking at much higher rates than the justice system identifies it. In the U.S., 1 in 3 women and 1 in
6 men report experiencing stalking in their lifetimes, with the vast majority stalked by someone they
know.
ii
Stalking frequently co-occurs with other crimes and is a risk factor for homicide.
iii
All stalkers
can be dangerous, but former or current intimate partners are generally more threatening, violent,
and interfering
iv
and may stalk their victims before, during, and/or after the relationship.
v
Because
they are so dangerous, it is important to identify and make findings about the criminal act of stalking
separate from and in addition to concurring abusive conduct in intimate partner relationships.
Stalking is often part of the coercive control tactics used by intimate partner violence offenders to
maintain control over victims and it is essential to identify and name stalking in these
cases. It is also important to note that stalkers target acquaintances, friends, family,
employees, students, and people they have never met.
Stalking is one of the top ten risk factors for intimate partner homicide, with a three-fold
increase in homicide risk when present.
vi

Judicial Officer Guide: Responding to Stalking Page 4
In one study, female victims in more than 75% of attempted and completed intimate partner
homicides had been stalked by the same offender during the previous year.
vii
• Among those who had been stalked, roughly 90% had also been physically abused.
viii
• More than half had reported their stalking to the police before they were killed.
ix
B. STALKING RELATIONSHIPS & DYNAMICS
The largest national survey on
stalking victimization (from the
Centers for Disease Control and
Prevention) reports that the vast
majority of stalking victims know the
offender.
x
This means that in the vast majority
of cases, stalkers know their victims
and likely have unique and intimate
knowledge about victims’
vulnerabilities and fears. It is vital to
understand the context of the
situation to be able to determine if a reasonable person in the victim’s contextual situation would feel
fear after experiencing the repeated targeted behaviors. When there is a history of violence and the
victim has gone to significant lengths to avoid any encounters with the offender, even a seemingly
friendly note or gift is an alarming signal that those efforts have
been unsuccessful and the offender poses a threat. It is also
important to note that some victims do not avoid all encounters
with the offender; instead they continue to have contact and
engage with the stalker as a safety strategy, to know what the
offender is doing, thinking, and/or planning, in order to plan or
negotiate accordingly for their safety.
C. STALKING IN OTHER CRIMES & CASES
Stalking behaviors can arise in a wide range of court cases, including domestic violence, sexual
assault, protection orders, custody, divorce, child welfare, employment, human trafficking, and
immigration cases, as well as other family, civil, or criminal court matters. Many crimes frequently
co-occur with stalking, including trespassing, burglary, computer crimes, nonconsensual distribution
of intimate images, vandalism, threats of bodily harm, voyeurism, and witness intimidation.
3%
6%
20%
9%
44%
32%
4%
9%
19%
8%
41%
43%
Person of Authority
Family Member
Stranger
Brief Encounter
Acquaintance
Current/Former
Intimate Partner
Stalking Victim & Offender Relationships
x
Female Victims
Male Victims

Judicial Officer Guide: Responding to Stalking Page 5
• Stalking can appear in any type of case and it is
particularly important to look for indicators of stalking
in cases where the parties know one another and/or
there is evidence of ongoing harmful contact.
• The more access to and information about the victim
that the offender has, the more dangerous and
threatening they can — and are likely to — be;
research shows that intimate partner stalkers use
violence and threats the most, followed by
acquaintance stalkers, and then strangers.
xi
o Intimate partner stalkers are more likely (than
stalkers with other relationships to victims) to
physically approach the victim; be interfering,
insulting, and threatening; use weapons;
escalate behaviors quickly; and re-offend,
making it vital to consider stalking whenever intimate partners are involved.
• In protection order and domestic violence related custody and divorce cases when the stalker is a
current or former partner, identifying and distinguishing stalking from other forms of intimate
partner violence also occurring in a case enhances the effectiveness of court orders. In criminal
domestic violence cases, evidence of stalking will be admissible at trial if relevant and allowable at
the sentencing phase of the criminal proceeding.
• Nearly 55% of women and 70% of men who are victims of stalking report it is unrelated to
intimate partner violence, showing that it is vital for judicial officers to recognize and respond to
stalking in a range of other contexts.
xii
This Judicial Guide will help judicial officers use concrete knowledge of stalking behaviors and how
these behaviors relate to other crimes to be better able to identify stalking in any type of case.
Whichever type of case stalking occurs in, judicial officers are encouraged to make specific findings
of fact regarding stalking and issue detailed orders designed to stop stalking behaviors, hold offenders
accountable, and prevent dangerous consequences.
II. UNDERSTANDING STALKING
Stalking is a course of conduct directed at a specific person that would cause a reasonable person to
feel fear for their own safety or the safety of others, and/or to feel emotional distress. Some
statutes define the number of incidents required to qualify as a stalking course of conduct, some
narrowly define fear, and some require that the stalker intentionally or knowingly causes fear.

Judicial Officer Guide: Responding to Stalking Page 6
All stalking statutes criminalize behaviors that are legal as single incidents, as well as abusive, coercive,
and controlling behaviors that may be illegal as single incidents. Therefore, it is crucial to pay
attention to the case’s context to accurately determine if the offender's behavior constitutes a
pattern that would cause a reasonable person to feel fear.
Stalking includes a wide range of threatening and disturbing behaviors and affects millions of people
in the U.S. each year. It can be done in-person, by using technology, or a combination thereof. As
with many crimes of interpersonal violence, offenders often target stalking victims because of
characteristics that make them less likely to report the crime and less likely to be believed or taken
seriously if they do report.
Women Men
Adults 18+
xiii
31% 16%
Young adults 18-24 years old
xiv
33% 28%
Adult victims (18+) with first stalking
experience before age 25
xv
58% 49%
Adult victims (18+) with first stalking
experience before age 18
xvi
24% 20%
Adult victims 18+
xvii
• Multiracial (non-Hispanic)
• American Indian or Alaska
Native (non-Hispanic)
• White (non-Hispanic)
• Black (non-Hispanic)
• Hispanic
• Asian or Pacific Islander (non-
Hispanic)
• 54%
• 42%
• 33%
• 30%
• 26%
• 24%
• 30%
• 30%
• 15%
• 20%
• 17%
• 9%
Bisexual women experience stalking twice as much as heterosexual women
and lesbian women experience stalking 25% more than heterosexual women,
in their lifetimes.
xviii
Gay men experience stalking twice as much as heterosexual men and bisexual
men experience stalking 40% more than heterosexual men, in their
lifetimes.
xix
Transgender and nonbinary/genderqueer undergraduate students experience
stalking 2.5 times more than all students.
xx
Persons with disabilities are twice as likely to experience stalking.
xxi
Women, young adults,
multiracial individuals,
people of color, individuals
with disabilities,
transgender and gender
nonbinary individuals, and
lesbian, gay, bisexual, and
queer individuals report
experiencing stalking at
higher rates. Additional
populations may also be
particularly vulnerable to
stalking. For example,
there is little research on
stalking and immigrant
communities, but specific
aspects of immigrant
women could be exploited
by abusers — cultural
differences, lack of
culturally-specific support
services, undocumented
or temporary immigration
status, limited English
proficiency, and living in
communities with limited
information about U.S.
laws and legal protections.

Judicial Officer Guide: Responding to Stalking Page 7
A. FRAMEWORK FOR UNDERSTANDING STALKING
It is extremely important to note that victims of stalking often do not identify their victimization as
stalking or harassment and are unlikely to use those words to describe what they are experiencing;
instead, they often describe the stalking behaviors and impacts.
xxiii
xxii
As such, it is important to use a
framework for assessing the presence of stalking rather than rely on victims to identify and name it.
Dr. TK Logan's multi-dimensional framework is an effective tool to assess stalking. The figure
below shows this framework and how the components of stalking are related to one another.
Note that the stalking offender’s intentional course of conduct directly results in the victim’s
reasonable fear, inspiring unwantedness as a byproduct of or reaction to the victim's fear.
B. COMPONENTS OF STALKING:
INTENTIONAL COURSE OF CONDUCT
To assess whether there is an intentional course of conduct that qualifies as stalking, Dr. Logan
explains it must meet two criteria, that:
• The behaviors can be classified as stalking tactics; and
• The duration, intensity, and/or frequency of those behaviors demonstrate an intentional
pattern of behavior.
Stalking tactics are classified into four groups (Surveillance, Life invasion, Intimidation, and
Interference through sabotage and attack) that are measured by their Duration, Intensity, and/or
Frequency. Together, stalking tactics and patterns of behavior corroborate intent,
xxiv
whether or not
the offender admits intent.

Judicial Officer Guide: Responding to Stalking Page 8
i.
SLII Stalking Tactics: Surveillance, Life Invasion, Intimidation, and Interference
through sabotage and attack
Stalkers often try to argue that their behavior is based on a legitimate purpose (to see the kids, to
share the car, to drive down the street, etc.), is a coincidence, or is not itself criminal behavior.
However, if their behavior is a pattern that shows the intent to survey, invade, intimidate, or interfere
with/sabotage the victim, then their actions legally meet the evidence-based definition of stalking.
When the offender targets a victim with specific incidents or tactics that the victim finds
frightening, this can be evidence of the offender’s intent to frighten them. SLII tactics can be done
in-person or through technology, and nearly half of all stalking victims experience both.
xxv
The examples of SLII tactics in Table 2 below pertain to all types of victim-stalker relationships. SLII
tactics can be part of the component of domestic violence called coercive control; when such tactics
are combined in a pattern of behavior that would cause a reasonable person to feel fear, these tactics
are both stalking and coercive control.
Table 2: Examples of SLII Stalking Tactics
SURVEILLANCE LIFE INVASION INTIMIDATION
INTERFERENCE
THROUGH SABOTAGE
OR ATTACK
• Follow
• Watch
• Wait
• Show up
• Tracking software or
devices
• Obtain information
about the victim
from others
• Have others stalk
the victim
• Monitor online
activity
• Access accounts
• Unwanted, non-
consensual contact
• Show up without
warning
• Property invasion
• Public humiliation
• Harass victim’s
friends/family
• Impersonate the
victim online
• Hack into the
victim’s accounts
• Explicit and implicit
threats
• Property damage
• Symbolic violence
• Forced
confrontations
• Threats to or
actually harm self
• Threats to harm
others
• Deportation threats
• Blackmail
• Threats to share
private information
• Threats to interfere
with employment,
finances, custody
• Financial, work
sabotage
• Ruining reputation
• Custody interference
• Keep victim from
leaving
• Road rage
• Attack victim’s
family, friends, pets
• Physical or sexual
attack
• Property damage
and/or vandalism
• Posting private
photos, videos,
information
• Controlling accounts
• Posing as victim and
creating harm

Judicial Officer Guide: Responding to Stalking Page 9
ii.
Stalking Perpetration: Duration, Intensity, Frequency
The framework also explains that stalkers utilize SLII tactics in a dynamic way that can be measured
by the Duration, Intensity, and Frequency of perpetration.
Duration
is how long the tactics have gone on — when the stalking started and
how long it has lasted.
Intensity
is the number of different tactics and locations that the stalker
employs.
Frequency
is how often the stalker makes their presence known — how often
the stalker approaches, confronts, and/or interferes in the victim’s life.
Whether the offender exhibits one continuous tactic or a variety of tactics, the longer the duration
and greater the intensity and frequency of any stalking tactics, the greater the risk of harm,
persistence, escalation, and life sabotage.
xxvii
xxvi
Data show greater victim psychological distress in
response to greater frequency of stalking and to any changes in stalker behavior, and escalation is
known to lead to greater violence.
iii.
Applying an Understanding of Stalking Tactics and Perpetration in Court Cases
Judicial officers will encounter stalking behaviors/tactics and will be able to identify and document
the duration, intensity, and frequency of stalking in a wide range of court cases. Stalking tactics are
not limited to criminal court cases and often appear in family court or other civil court cases,
including divorce, custody, guardianship, protection order, child welfare, employment, housing,
immigration, and other court actions, as well as administrative law proceedings. When stalking
behaviors are present and overlooked or not taken seriously by the court, the orders that the court
issues will not be effective in curbing stalking and other abusive behaviors, compromising victim
safety. On the other hand, identifying the presence of stalking in a family court or juvenile court
proceeding can help courts design better court orders that more effectively protect children and
domestic violence and stalking victims from ongoing harm. By routinely identifying stalking
behaviors, analyzing and documenting SLII tactics in court findings, and issuing court orders
designed to interrupt stalking behavior and hold offenders accountable, judicial officers can help
increase the safety of victims and their children.
The duration, intensity, and frequency analysis can assist with the determination of the offender’s
intent to instill fear or emotional distress and can inform the design of orders in family and civil court.
With this evidence and these findings, courts can specifically design court orders containing no-
contact provisions, mitigating direct contact between the victim and offender, and utilizing other

Judicial Officer Guide: Responding to Stalking Page 10
available safety measures. Courts can also
use such evidence and findings to better
inform child custody orders, rather than
granting access by default. Courts can also
refer victims to victim advocates who can
help them develop safety plans. Detailed
findings regarding the stalking behaviors and
their frequency, duration, and intensity help
appraise future judicial officers who hear
actions involving the same parties of the
severity of the abuse occurring in the case.
In criminal stalking cases, since the crime of stalking involves both a course of conduct and a result of
that conduct (fear or emotional distress on the part of the victim), it is important to determine what
mental state (or mens rea) is applicable both with respect to the conduct and to the result of that
conduct, since those, too, are elements of the crime that must be proved.
The criminal codes in many jurisdictions follow the Model Penal Code’s (MPC) culpability scheme,
which specifies the levels of culpability that must be proved with respect to acts or conduct that are
elements of a crime, as well as those pertaining to the effect or result of those acts. That scheme
classifies the mental elements of crimes as “purposeful,” “knowing,” “reckless,” or “negligent.”
xxviii
In
MPC jurisdictions, the applicable statutory provisions, together with the principles of statutory
construction, will determine which mental state must be proved with respect to acts or results of the
acts. The stalking statute may require, for example, that the
prosecution prove the defendant acted purposely with regard to
the acts constituting the course of conduct, but that the
defendant merely knew (or recklessly disregarded the risk) that
the victim would be placed in fear or would experience emotional
distress. On the other hand, it may require that the defendant
specifically intended for the victim to experience fear or
emotional distress.
Determining what must be proved with regard to the offender’s state of mind requires careful
reading of the stalking statute as well as any generally applicable provisions in the criminal code
related to culpability states or intent/mens rea and any relevant case law.
In jurisdictions that have not adopted the MPC culpability standards, the stalking statute may use
elements with a specific meaning (e.g., “willfully” or “maliciously”) that are defined by the
jurisdiction’s criminal code or in its case law. It may be important to determine whether the statute is
one of “general intent,” in which the defendant must intend only to commit the acts constituting the

Judicial Officer Guide: Responding to Stalking Page 11
course of conduct, or whether it is one of “specific intent,” in which case the defendant must also
intend the result of the conduct — the victim’s fear or emotional distress. The offender's requisite
intent may be satisfied by proving that:
• The offender's behavior can be classified as stalking tactics; and
• The duration, intensity, and frequency show a pattern of behavior.
If the offender’s actions were particularly frightening or upsetting because of past history or
information that they possessed about the victim — for example, making threats that play on a
particular fear — this shows the offender’s knowledge and intent.
Some jurisdictions consider past convictions admissible in criminal stalking cases as part of the
documentation of repeated behaviors; others do not. In a civil, family, or administrative law case,
such rules disallowing past convictions would not apply.
C. COMPONENTS OF STALKING:
REASONABLE FEAR
The second part of the framework is victim fear. Many statutes use the reasonable person standard
of feeling fear for their own safety or the safety of others, or feeling emotional distress.
Determining the reasonableness of fear includes assessing:
• The specific implicit or explicit threats;
• The context of those threats; and
• Victim fear or concern for safety.
Fear is central to stalking and it is highly contextual: what one
person finds frightening may not be frightening to another. To
determine reasonable fear, it is vital to determine the context of the
situation and understand the meaning of a situation or action to the
victim. In stalking cases, many of the behaviors are only frightening
to a victim because of their relationship with the stalker.
Victims react to stalkers in a variety of ways and fear is often
masked by other emotions: anger, frustration, hopelessness, despair,
or apathy. Some may minimize and dismiss their stalking as “no big
deal.” It is helpful to consider how victims change their behaviors to
cope with the stalking. At a minimum, these are signs that the
stalker’s behaviors are unwanted and the victim is resisting the contact. Evidence and corroboration
of the victim’s fear and resistance can be found by considering accommodations and changes the
victim has made to their life.

Judicial Officer Guide: Responding to Stalking Page 12
Accommodations and changes the victim has made to their life might include:
• Time spent obtaining a protection order
• Screening phone calls
• Relocation
• Efforts to keep
their address or location a secret
• Changing their own phone numbers,
email addresses, and/or social media
accounts
• Blocking phone numbers, email
addresses, and/or social media accounts
• Changes to device settings
• Time accessing support services
• Confidentially filing the victim’s
own immigration case to sever
reliance on the stalker’s
sponsorship
• Finances spent on safety devices
or accommodations
• Increased security and/or privacy
measures
• Asking friends, family, or
professionals for help
• Changes to schedule, routine, and/or
route/method of transport
• Avoiding locations or activities
• Financial impacts like employment
consequences
• Costs for repair or replacement of
damaged property, or immigration or
identity documents
• Informing work, daycare, school,
apartment building, religious
space, and/or others of the
situation and/or asking for
accommodations
• Taking steps to remedy identity theft
D. COMPONENTS OF STALKING:
UNWANTEDNESS
The third part of the framework is that the stalker’s behavior is unwelcome and the victim does not
want it to be happening. Indicators of this unwantedness can include the victim stating that they
want the stalker to stop, as well as steps they take to resist contact with the stalker. When a victim
makes changes in their life because of the stalker’s behavior, it is a clear sign that those behaviors are
unwanted.
Note that victims may show signs of unwantedness while also engaging with their stalker. Victims use
a variety of strategies to cope with stalking, including confronting the stalker, appeasing the stalker,
denying the stalking is happening, distracting themselves, or taking steps to try to increase their
safety. It is important to note that some victims continue to have contact with and engage with the
stalker as a safety strategy. They are gathering information, assessing the offender’s state of mind,
and negotiating for their safety. Contact on the part of the victim does not mean that the victim is
not in fear or that the stalker’s behaviors are wanted. In fact, it may indicate that the victim is very

Judicial Officer Guide: Responding to Stalking Page 13
afraid of the offender and is
contacting the offender to be
able to assess and plan the steps
they will take to increase safety
for themselves and their
children.
xxix
Stalkers may be notified that their
behavior is unwanted by direct, formal means (like a protection order or
communication from the victim) or more indirectly (like their victim not
responding to their efforts at communication or avoiding them). Whether
the stalker is formally notified or should be picking up on social norms that
their behavior is unwanted, if they continue to persist it is an important red flag
for the victim’s safety as well as a clear sign that the stalker’s course of conduct is deliberate and
intentional.
E. TECHNOLOGY-FACILITATED STALKING
Technology-facilitated stalking (cyber-stalking) should be given the same consideration and concern
as in-person stalking. Nearly half of all stalking cases involve both in-person and technology-
facilitated stalking.
xxx
Offenders both use and misuse technology to facilitate
their stalking. Technologies and tactics used by offenders are constantly evolving
and may seem impossible or unrealistic, but stalking offenders are creative in the
pervasive ways they monitor, surveil, contact, control, and isolate victims, as well
as the ways they damage victims’ credibility or reputation. Staying abreast of
evolving technology allows for the full scope of the offender’s actions to be
considered.
The impact of technology-facilitated stalking is vast and just as invasive,
threatening, and fear-inducing as in-person stalking. Victims of technology-
facilitated stalking often report higher levels of fear than individuals who
experience in-person stalking, and are just as concerned for their safety.
xxxi
Technology used to stalk can include but is not limited to: telephones,
computers, tablets, mobile devices, software, the internet, email, social media,
messaging applications, smart home devices, recording devices, tracking devices,
or other digital electronic devices and software.
In Table 3 below, common technology-facilitated stalking tactics are categorized using the SLII
framework.
xxix

Judicial Officer Guide: Responding to Stalking Page 14
Table 3: Examples of Technology-Facilitated Stalking SLII Tactics
SURVEILLANCE LIFE INVASION INTIMIDATION
INTERFERENCE
THROUGH SABOTAGE
OR ATTACK
• Smart home devices
• Tracking software
• GPS or Bluetooth
tracking devices
• Cameras or
audio/video
recording devices
• Monitoring online
activity
• Accessing online
accounts
• Unwanted contact
online, through text
messages or phone
calls, other
platforms
• Impersonating
victim
• Hacking victim’s
accounts
• Impersonating
others to access the
victim
• Online threats
• Blackmail
• Sextortion
• Threats to release
private information,
photos, or videos,
real or fake
• Threats to interfere
with online accounts
• Posting private
photos, videos,
information online,
real or fake
• Spreading rumors
online
• Doxing (publicly
posting personally
identifiable
information)
• Swatting (prank call
to emergency
services)
• Controlling online
accounts
• Posing as victim and
creating harm
• Using technology to
encourage others to
harm the victim
III. ASSESSING RISK IN STALKING CASES
When reviewing a stalking case, there are 14 factors to consider in assessing the risk posed to victims.
Evidence-based research has found that the presence of or increase in any of the factors in Table 4
below contributes to increased risk of current and future harm to the stalking victim.
xxxii
Note that
there may be additional risk factors unique to a case that do not fit neatly into one of these
categories but that should still be considered.
The Stalking and Harassment Assessment and Risk Profile (SHARP) is a web-based tool that
examines these risk factors and provides a situational risk profile (available at
www.CoerciveControl.org). This risk assessment is useful for several considerations: pretrial

Judicial Officer Guide: Responding to Stalking Page 15
detention and bail conditions, which cases may demand greater attention, and sentencing and post-
sentencing (e.g., probation or parole).
Table 4: Stalking Risk Assessment Factors
IV. CO-OCCURRING AND INTERCONNECTED CRIMES
It is critical to consider how stalking relates to and intersects with other criminal offenses to help to
ensure that the defendant is held appropriately accountable for the full scope of their behaviors and
criminal conduct, and the ensuing harm to the victim. Assessments to identify stalking behavior
should be done in any case that has the potential for stalking behaviors, but specifically in
emergency protection order petitions, domestic violence protection order hearings, domestic
violence related custody and divorce cases, and employment-based cases. In employment-based
sexual assault cases, assessments for stalking and other crimes can be crucial to identifying the full
range of criminal or discriminatory behavior and retaliation perpetrated. Since stalking is a continuing
crime, it may include incidents that in a criminal prosecution would otherwise be barred by the
statute of limitations. Those incidences can be included in stalking prosecutions because the
limitations period for a continuing crime does not begin to run until the crime has concluded.
A. STALKING & INTIMATE PARTNER VIOLENCE
Stalking often co-occurs with domestic/intimate partner violence and can be an indicator of other
forms of violence. When a domestic abuser repeatedly engages in physical, sexual, emotional, or
psychological abuse against a victim, that may also be stalking. A common aspect of intimate
partner violence is coercive control, and stalking tactics are often part of that coercive control.

Judicial Officer Guide: Responding to Stalking Page 16
When abusers use stalking tactics to intimidate and control their victims, engaging in a pattern of
behavior that would cause a reasonable person to feel fear, abusers are engaging in both stalking and
coercive control.
xxxiii
Compared to non-intimate partner stalkers, intimate
partner stalkers are more likely to:
• Approach and confront victims more frequently;
xxxiv
• Be more intrusive in the victim’s life;
xxxv
• Use a wider range of stalking tactics;
xxxvi
• Follow through on threats of violence;
xxxvii
• Continue stalking for a longer period of time;
xxxviii
• Reoffend after court intervention;
xxxix
and
• Reoffend more quickly.
xl
Among victims stalked by an intimate partner, 74% report violence and/or coercive control during
the relationship.
xli
Prior to attempted or completed intimate partner femicide, the most common use
of the criminal justice system was reporting partner stalking.
xlii
Stalking is not simply the offender having a difficult time letting go of the relationship. It is vital to
recognize the offender’s history of controlling and dangerous behaviors as well as the fear that the
stalking generates in the victim. Even when there is no physical violence, stalking is still dangerous,
traumatic, and criminal.
B. STALKING & HUMAN TRAFFICKING
Human trafficking often involves co-occurring stalking behavior, where the stalking may be a tactic
to coerce or isolate the victim, or to intimidate the victim or witnesses. History is important in cases
of human trafficking (as well as any other crime in which the offender and victim had a relationship of
any duration), providing the offender with the opportunity and motive to engage in repetitive acts in
the course of targeting or maintaining control over the victim. Given the various methods of coercive
control used by traffickers of sex and labor, it is difficult to imagine a human trafficking case that
does not also involve stalking.
When considering cases of human trafficking, it is important for judicial officers to carefully consider
whether the offender’s behavior also constitutes stalking and if so, to make detailed findings in court
orders about stalking tactics, duration, and impacts on the victim.
xxxiii

Judicial Officer Guide: Responding to Stalking Page 17
C. STALKING & WITNESS INTIMIDATION
Stalking as a means of witness intimidation may be employed by human traffickers, perpetrators of
domestic violence, and offenders of other crimes, as well — ranging from drug offenses and gang
violence to white-collar crime. Offenders may use stalking to keep victims from reporting to
authorities. Offenders or their allies may repeatedly drive by the witness’s home, park on the
witness’s street, or make threats against the witness or the witness’s family, including immigration-
related threats. Offenders may use social media to threaten witnesses or expose their cooperation
with the justice system on social media or other websites. Repetitive acts of this type may be
sufficient to support a stalking finding.
Considering witness intimidation — especially after the victim has reported to law enforcement or
applied for a protection order — is a vital piece of a stalking case; stalkers often threaten victims
about reporting to and/or participating in the justice system. Considering post-intervention stalker
behavior is a key part of a case, and stalking may actually increase during this time.
Judicial officers should carefully consider both stalking and witness intimidation whenever
considering one or the other.
D. STALKING & SEXUAL VIOLENCE
Sexual violence and stalking intersect in a variety of ways. Offenders may use sexual violence as part
of a stalking course of conduct, with SLII tactics such as those explained in Table 5 below.
Fear of sexual assault is covered under most stalking
statutes. Some stalkers sexually assault their victims as
part of the ongoing stalking, some begin stalking their
victims after they sexually assault them, some threaten
or plan to sexual assault their victim, and some solicit a
third party to sexually assault their victim.
xliii
When sex offenders select, groom, shame, intimidate, and threaten their victims into silence over a
period of weeks, months, or years, that is likely stalking.
xliii

Judicial Officer Guide: Responding to Stalking Page 18
Table 5: Examples of Sexually Violent SLII Stalking Tactics
SURVEILLANCE LIFE INVASION INTIMIDATION
INTERFERENCE
THROUGH SABOTAGE
OR ATTACK
• As part of planning a
sexual assault
• Monitoring a victim
after a sexual assault
• Voyeurism
• Unwanted contact
or communication of
a sexual nature or
about a sexual
assault
• Sexual harassment
• Nonconsensual
distribution of
intimate images
• Indecent exposure
• Spreading sexual
rumors
• Publicly humiliating
or shaming or
embarrassing the
victim with sexual
language or
information
• Threats of sexual
violence or sharing
sexual information
• Threats of violence
or sabotage if the
victim refuses to
perform sexual acts
• Blackmailing in
exchange for sexual
activity or photos
• Sexual assault
• Sexual harassment
• Stealing sexual
photos or videos
• Sharing sexual
photos or videos
without consent
• Sexually trafficking
or exploiting the
victim
E. STALKING & PROTECTION ORDER VIOLATIONS
Stalking is associated with increased protection order violations, across types of orders including
protection orders issued to stop family violence, sexual assault, and stalking. In one study, stalking
was also associated with higher levels of fear; researchers compared victim fear across different
situations, finding that victims were more fearful when their protection order was violated and they
had been stalked, compared with when their protection order was violated and they had not been
stalked, and compared with when their protection order
was not violated at all.
xliv
xlv
Enforcement is a crucial component of protection
order effectiveness. Effective enforcement of orders in
stalking cases can increase victim safety and offender
accountability, and reduce general costs to society. The
xlv

Judicial Officer Guide: Responding to Stalking Page 19
relief of distress provided by court orders is significant to victims. In one study, 58% of women
experienced a protective order violation but the majority still said the protective order was extremely
(51%) or fairly (27%) effective, and that they felt extremely (43%) or fairly (34%) safe.
xlvi
Victims cannot violate their own protection orders because the orders circumscribe only the
offender’s behavior, not the victim’s.
V. STALKING, COERCIVE CONTROL, AND BATTERY OR
EXTREME CRUELTY
Table 6 below outlines the differences and overlap between stalking, coercive control, and battery or
extreme cruelty.
xlvii
Coercive control has been found by researchers to be dangerous and is becoming a part of the
definition of domestic violence in protection order and other family court cases in some
jurisdictions.
xlviii
California’s domestic violence protection order and family laws define coercive
control as, “a pattern of behavior that in purpose or effect unreasonably interferes with a person’s
free will and personal liberty.”
xlix
Under this law, coercive control is a basis for issuance of a protection
order and coercive control creates a rebuttable presumption that “an award of child custody to a
party who has engaged in coercive control is detrimental to the best interests of the child.”
l
Stalking
behaviors are also forms of coercive control.
Battering or extreme cruelty (the immigration law definition of domestic violence) has historically
been recognized by courts, especially in the contest of “for cause” divorce cases, as characteristic of
the forms and patterns of emotional abuse causing harm to the victim.
li
A strong foundational
understanding of each of these types of behaviors offers all courts — state, federal, Tribal,
immigration — more opportunities to identify facts that constitute stalking, coercive control, and/or
extreme cruelty. This then allows the courts to issue orders designed to halt this dangerous, harmful,
and potentially criminal behavior, and to support victim safety.

Judicial Officer Guide: Responding to Stalking Page 20
Table 6: Comparing Stalking, Coercive Control, and Battery or Extreme Cruelty
Stalking
Coercive Control
Battery or Extreme Cruelty
Definition: Engaging in a course of
conduct directed at a specific person
that would cause a reasonable person
to fear for their safety or the safety
of others, or suffer substantial
emotional distress.
Forms of stalking include:
• Surveillance
• Life invasion
• Intimidation
• Interference through sabotage
or attack
Behaviors that demonstrate stalking:
• Monitoring movement,
communications, daily behavior,
finances, and services accessed
• Harassing friends and family
• Sabotaging employment,
schooling, or immigration status
• Showing up unexpectedly or
refusing to leave a location
• Invading or vandalizing property
• Ruining reputation
• Humiliating a victim or forcing
a confrontation
• Accessing online accounts or
impersonating a victim
Definition: Strategies designed to
retain privileges and establish
domination in a partner’s personal life
based on: fear, dependence, and
deprivation of basic rights and
liberties.
Forms of coercive control include:
• Intimidation
• Degradation/emotional abuse
• Isolation
• Control
• Physical and/or sexual assault
Behaviors that demonstrate coercive
control:
• Social isolation
• Depravation of food, medicine
• Neglect
• Controlling or regulating
movement, communications,
daily behavior, finances, and
access to services
Definition under U.S. Immigration Law:
Being the victim of any act or a
threatened act of violence, including any
forceful detention which results or
threatens to result in physical or mental
injury. Psychological or sexual abuse or
exploitation, including rape, molestation,
incest (if the victim is a minor), or
forced prostitution shall be considered as
acts of violence. Other abusive actions
may also be acts of violence under this
rule. Acts or threatened acts that, in and
of themselves, may not initially appear
violent may be part of an overall pattern
of violence.
lii
Any act that constitutes a crime,
including threats and attempts, or is
conduct that could result in issuance of a
protection order under state law,
amounts to “battering” under U.S.
immigration law.
Battery/extreme cruelty can manifest in
other crimes, so findings for battery can
be made in addition to stalking and
coercive control.
Behaviors that constitute
battery/extreme cruelty under
immigration law include:
• Stalking
• Physical or sexual assault
• Attempted assaults
• Striking someone with an object
• Hitting, slapping, punching,
pinching, biting, or grabbing
•
Threats of violence

Judicial Officer Guide: Responding to Stalking Page 21
Stalking
Coercive Control
Battery or Extreme Cruelty
Behaviors that may demonstrate stalking and coercive control:
• Monitoring communications (calls, messages, emails)
• Monitoring social media or online presence
• Compelling by force, threat of force, or intimidation
• Interfering in or sabotaging the immigration process, employment, or
schooling
• Showing up unannounced (to school, work, the gym, etc.)
• Tracking phone, computer, or tablet use
• Public humiliation, in-person or online
• Threats to or actually harming self
•
Threats to harm others
Behaviors that may demonstrate coercive control and battery/extreme cruelty:
• Degradation
liii
• Neglect
• Immigration related abuse
• Threats of deportation
•
Depravation of food or medicine
Behaviors that may demonstrate stalking, coercive control, and battery/extreme cruelty:
• Physical, sexual, or verbal abuse
• Using or threating to use, or displaying a weapon
liv
• Property invasion or destruction
• Using children as a tool toward the other parent
• Financial or work sabotage
•
Ruining reputation
VI. CAPTURING STALKING TACTICS IN RULINGS
Making findings of stalking and documenting stalking behaviors in court orders identifies and
confirms that the conduct that contributed to the finding of stalking is criminal and was not a one-
time event, but rather part of an intentional campaign against the victim that can be expected to
continue if it is not prevented. Since stalking cases take time to develop, it is important that judicial
officers also make findings regarding criminal, abusive, and other conduct that is harmful to others in
criminal, family, and civil court cases as well as administrative law cases. These findings provide a
record and documentation that can help show the trajectory of escalation, which is important for
future judicial proceedings including but not limited to stalking prosecutions.

Judicial Officer Guide: Responding to Stalking Page 22
There are important details for judicial officers to include in court findings and when issuing
protection orders. Some courts use computer systems with prepared form orders that can be easily
distributed to law enforcement electronically, which often have limited space available that is not
sufficient for the important details necessary when stalking is present. In stalking cases, judicial
officers should consider adding addendums or attachments to these orders or issuing more detailed
court orders.
When stalking is perpetrated against an intimate partner, child, family member, or other person
covered by state protection order statutes, the stalking victim is eligible for a protection order.
lv
Consider orally informing the offender of conditions and prohibitions for protection orders and bail in
court, particularly the prohibition from possessing firearms, ammunition, and related permits and
their associated verifiable surrender. Also consider orally informing the offender that violations can
result in revocations of bail, probation, etc. and may be the basis for (additional) criminal charges.
Use qualified interpreters in any criminal, family, or civil case involving offenders or victims who have
limited English proficiency. Having court orders translated into the languages spoken by the offender
and/or by the victim promotes greater compliance with court orders and victim safety.
Both protection orders and bail conditions should:
Include no-contact provisions that carefully specify prohibitions on indirect as well as
direct contact, including contact through the use of technology and social media, and
any other conditions (e.g., GPS monitoring or restrictions on use of digital devices)
that will help to ensure the victim’s safety.
Specify that “no contact” includes indirect contact and contact through third parties,
as well as social media posts about, or directed toward, the victim.
Prohibit contact with members of the victim’s family or household and, in appropriate
cases, the victim’s employer and named friends of the victim.
Prohibit the offender from monitoring, tracking, or surveilling the victim, by use of
technology or otherwise.
List any locations frequented by the victim and specify the distance that the stalking
offender must stay away from these locations.
Address when the offender and victim regularly frequent the same places (e.g., a church or a gym) —
the order should bar the offender from those locations completely except during times specified in
the court order (designing the order so that the victim is safe to be at the location except
during the hours that the offender is authorized to be there).

Judicial Officer Guide: Responding to Stalking Page 23
Specify that if the offender arrives at a public location and the victim is present, the
offender must promptly depart.
Prohibit the offender from possessing firearms, ammunition, and any firearms permits,
and should require verifiable surrender of any of these that the offender currently
possesses.
• Research suggests that when abusers have easy access to guns, the risk of firearms threats
and homicide increases;
lvi
•
Some jurisdictions have protocols in place for firearms surrender; if a jurisdiction lacks such a
protocol, resources and technical assistance for establishing such procedures can be found at
the National Domestic Violence and Firearms Resource Center, at
www.preventdvgunviolence.org.
Require the Prosecuting Attorney in a criminal case be informed of any attempt made by
the Defendant to purchase a weapon that is rejected by a Federal database.
Require electronic monitoring of the offender (e.g., ankle bracelet) and regular in-
person reporting to probation.
Prohibit the use of alcohol or recreational drugs.
It can be very useful for stalking victims and other victims of domestic and sexual violence to receive
court orders that protect them from offenders’ ongoing stalking, abusive actions, and criminal
conduct. Stalking victims may qualify for civil protection orders and bail conditions can be set in
criminal cases that offer victims protection. Due to the differences between protection orders and
bail conditions, it can be helpful for stalking victims to receive protections offered by both types of
court orders. Protection orders may be more readily enforceable than bail conditions because
violation of a civil protection order is a crime that can lead to the offender’s arrest. Similarly,
contempt citations in civil cases can be used to hold offenders accountable when they violate a court
order. Enforcement of bail conditions, in contrast, may require a motion to revoke bail. The
associated delay in enforcement can potentially endanger the victim, since the offender may remain
at liberty while the motion is pending. There is also a difference in the duration of the protection
offered: protection orders remain in place until they expire and can often be extended, while bail
conditions remain in place only during the pendency of the criminal proceedings.
Any violations should result in prompt action to report the protection order violation to law
enforcement and to initiate an enforcement action to revoke bail set in criminal cases, particularly
when the violation is one that poses a risk to the victim or to anyone else.

Judicial Officer Guide: Responding to Stalking Page 24
A. EXAMPLE OF STALKING FINDINGS
Petitioner, name, is a victim of stalking. Respondent, name, has utilized [insert stalking tactics
categories, i.e., Surveillance, Life Invasion, Intimidation, Interference through sabotage or attack]
through the following behaviors [list the behaviors that fall under the respective category]. These
behaviors are found to be stalking tactics. Respondent, name, has executed these behaviors that
display a pattern of stalking [name the pattern; include frequency, duration, and intensity].
Respondent’s pattern of behavior escalated and resulted in greater threat and/or violence against
Petitioner, name. Respondent’s actions constitute stalking [insert citation to statutory definition].
HAVING MADE THESE FINDINGS… [Insert detailed specific orders to stop that specific
behavior].
B. EXAMPLE OF COERCIVE CONTROL FINDINGS
Petitioner, name, is a victim of coercive control. [Add citation to state law, if any]. Respondent,
name, utilized [name the coercive control examples
lvii
]. Respondent’s behavior is abusive and/or
coercive and amounts to coercive control strategies. Petitioner experienced [describe the details of
petitioner’s fear; dependence; and deprivation of basic rights and liberties] because of Respondent’s
behavior. Respondent intended their abusive and/or coercive controlling behavior would retain
privileges and establish domination in Petitioner’s life. HAVING MADE THESE FINDINGS…
[Insert detailed specific orders to stop that specific behavior].
VII. FOR MORE INFORMATION
For additional resources and support on responding to stalking, visit www.StalkingAwareness.org and
contact SPARC at tta@stalkingawareness.org. SPARC’s website has Recorded Trainings for a
variety of audiences and resources not only for judicial officers on responding to stalking, but also
resources to share with partners — including Prosecutors, Law Enforcement, Corrections/Probation,
and Victim Services — to better work together to build stalking cases, support victims, and hold
offenders accountable.

Judicial Officer Guide: Responding to Stalking Page 25
ENDNOTES
i
SPARC provides information on stalking statutes in each U.S. jurisdiction: https://www.stalkingawareness.org/map
ii
Smith, S.G., Basile, K.C., & Kresnow, M. (2022). The National Intimate Partner and Sexual Violence Survey (NISVS): 2016/2017 Report on Stalking.
Atlanta, GA: National Center for Injury Prevention and Control, Centers for Disease Control and Prevention.
iii
Spencer, C.M. & Stith, S.M. (2018). Risk Factors for Male Perpetration and Female Victimization of Intimate Partner Homicide: A Meta-Analysis.
Trauma, Violence, & Abuse, 21(3), 527-540.
iv
Mohandie, K., Meloy, J., McGowan, M., & Williams, J. (2006). The RECON typology of stalking: Reliability and validity based upon a large sample of
north American stalkers. Journal of Forensic Science, 51(1), 147-155.
v
Tjaden, P. & Thoennes, N. (1998). Stalking in America: Findings from the national violence against women survey (NCJ#169592). Washington, DC:
National Institute of Justice Centers for Disease Control and Prevention.
vi
Spencer, C.M. & Stith, S.M. (2018). Risk Factors for Male Perpetration and Female Victimization of Intimate Partner Homicide: A Meta-Analysis.
Trauma, Violence, & Abuse, 21(3), 527-540.
vii
McFarlane, J., Campbell, J.C., Wilt, S., Ulrich, Y., & Xu, X. (1999). Stalking and Intimate Partner Femicide. Homicide Studies, 3(4), 300-316.
viii
Id.
ix
Id.
x
Smith, S.G., Basile, K.C., & Kresnow, M. (2022). The National Intimate Partner and Sexual Violence Survey (NISVS): 2016/2017 Report on Stalking.
Atlanta, GA: National Center for Injury Prevention and Control, Centers for Disease Control and Prevention.
xi
Mohandie, K., Meloy, J., McGowan, M., & Williams, J. (2006). The RECON typology of stalking: Reliability and validity based upon a large sample of
north American stalkers. Journal of Forensic Science, 51(1), 147-155.
xii
Smith, S.G., Basile, K.C., & Kresnow, M. (2022). The National Intimate Partner and Sexual Violence Survey (NISVS): 2016/2017 Report on
Stalking. Atlanta, GA: National Center for Injury Prevention and Control, Centers for Disease Control and Prevention.
xiii
Id.
xiv
Id.
xv
Id.
xvi
Id.
xvii
Id.
xviii
Chen, J. Walters, M.L, Gilbert, L.K., & Patel, N. (2020). Sexual violence, stalking, and intimate partner violence by sexual orientation, United States.
Psychological of Violence, 10(1), 110-119.
xix
Id.
xx
Cantor, D., et al. (2020). Report on the AAU Climate Survey on Sexual Assault and Sexual Misconduct. Westat.
xxi
Reyns, B. W., & Scherer, H. (2018). Stalking victimization among college students: The role of disability within a lifestyle-routine activity framework.
Crime & Delinquency, 64(5), 650-673.
xxii
Jordan, C. E., Wilcox, P., & Pritchard, A. J. (2007). Stalking acknowledgement and reporting among college women experiencing intrusive
behaviors: Implications for the emergence of a “classic stalking case”. Journal of Criminal Justice, 35(5), 556-569.
xxiii
Logan, TK & Walker, R. (2017). Stalking: A Multi-dimensional Framework for Assessment and Safety Planning. Trauma, Violence and Abuse, 18(2),
200-222.
xxiv
Id.
xxv
Truman, J.L., & Morgan, R.E. (2021). Stalking Victimization, 2016. Washington, DC: US DOJ, Bureau of Justice Statistics, Special Report.

Judicial Officer Guide: Responding to Stalking Page 26
xxvi
Logan, TK & Walker, R. (2017). Stalking: A Multi-dimensional Framework for Assessment and Safety Planning. Trauma, Violence and Abuse, 18(2),
200-222.
xxvii
Id.
xxviii
See, Model Penal Code § 2.02
xxix
Keith, A. (2 January 2022). Probable cause found for first degree stalking. Bonner County Daily Bee.
https://bonnercountydailybee.com/news/2022/jan/02/probable-cause-found-first-degree-stalking
.
xxx
47% of stalking cases involve both in-person and technology enabled tactics (Truman, J.L., & Morgan, R.E. (2021). Stalking Victimization, 2016.
Washington, DC: US DOJ, Bureau of Justice Statistics, Special Report).
xxxi
Fissel, E. R., & Reyns, B. W. (2020). The Aftermath of Cyberstalking: School, Work, Social, and Health Costs of Victimization. American Journal of
Criminal Justice, 45(1), 70-87.
xxxii
Logan, TK & Walker, R. (2017). Stalking: A Multi-dimensional Framework for Assessment and Safety Planning. Trauma, Violence and Abuse, 18(2),
200-222.
xxxiii
Tjaden, P. & Thoennes, N. (1998). Stalking in America: Findings from the national violence against women survey (NCJ#169592). Washington,
DC: National Institute of Justice CDC.
xxxiv
Davis, K., Ace, A., & Andra, M. (2000). Stalking perpetrators and psychological maltreatment of partners: Anger, jealousy, attachment insecurity,
need for control, and break-up context. Violence and Victims, 15(4), 407-425.
xxxv
Mohandie, K., Meloy, J., McGowan, M., & Williams, J. (2006). The RECON typology of stalking: Reliability and validity based upon a large sample
of north American stalkers. Journal of Forensic Science, 51(1), 147-155.
xxxvi
Johnson, M. & Kercher, G. (2009). Identifying predictors of negative psychological reactions to stalking victimization. Journal of Interpersonal
Violence, 24(5), 886-882.
xxxvii
Palarea, R., Zona, M., Lane, J. & Langhinrichsen-Rohling, J. (1999). The dangerous nature of intimate relationship stalking: Threats, violence and
associated risk factors. Behavioral Sciences and the Law, 17, 269-283.
xxxviii
Brewster, M. (2003). Power and control dynamics in pre-stalking and stalking situations. Journal of Family Violence, 18, 4, 207-217.
xxxix
Rosenfeld, B. (2003). Recidivism in stalking and obsessional harassment. Law and Human Behavior, 27(3), 251-265.
xl
Id.
xli
Brewster, M. (2003). Power and control dynamics in pre-stalking and stalking situations. Journal of Family Violence, 18(4), 207-217.
xlii
McFarlane, J., Campbell, J.C., & Watson, K. (2001). The Use of the Justice System Prior to Intimate Partner Femicide. Criminal Justice Review,
26(2), 193-208.
xliii
Brady, P. Q., & Woodward Griffin, V. (2019). The Intersection of Stalking and Sexual Assault Among Emerging Adults: Unpublished Preliminary
Results. mTurk Findings, 2018.
xliv
Logan, TK, Walker, R., Hoyt, W., & Faragher, T. (2009). The Kentucky civil protective order study: A rural and urban multiple perspective study of
protective order violation consequences, responses, & costs. (NCJ Publication # 228350). Washington, D.C.: National Institute of Justice, U.S.
DOJ.
xlv
Logan, TK, & Walker, R. (2009). Civil Protective Order Outcomes: Violations and Perceptions of Effectiveness. Journal of Interpersonal Violence,
24(4), 675-692.
xlvi
Id.
xlvii
For more information, see: Orloff, L.E., Roberts, B., & Gitler, S. (2015). “Battering or Extreme Cruelty” Drawing Examples from Civil Protection Order
and Family law Cases. National Immigrant Women’s Advocacy Project, American University, Washington College of Law.
https://niwaplibrary.wcl.american.edu/pubs/extreme-cruelty-examples-protection-order-2
; Dutton, M.A., & Goodman, L.A. (2005). Coercion in
Intimate Partner Violence: Toward a New Conceptualization, Sex Roles, 52(11/12), 743-756.
Judicial Officer Guide: Responding to Stalking Page 27
xlviii
Hawaii HB 2425 (September 15, 2020) Hawaii Revised Statutes Sections 431:10-217.5(e); 432:1-101.6(e); 432:2-103.5(e); 432C-27; 586-1;
California SB 1141 (September 29, 2020) California Family Code Section 6320; Connecticut SB 1091 (June 28, 2021); Connecticut Statues
46b-1, 46b-15; 46b-38a; 46b-54; 46b-56; 54—64(a).
xlix
Domestic violence: coercive control, No. 1141, S.B. 1141, Session 2019-2020 (C.A. 2020).
l
Id.
li
For more information, see: Battering or Extreme Cruelty: Drawing Examples from Civil Protection Order and Family Law Cases (September 12,
2015) https://niwaplibrary.wcl.american.edu/pubs/extreme-cruelty-examples-protection-order-2
; Laura Luis Hernandez v John Ashcroft 9th
Circuit Court of Appeals (October 7, 2003) https://niwaplibrary.wcl.american.edu/pubs/9th-cir-hernandez-extreme-cruelty-10-7-03.
lii
See VAWA self-petition regulations: 8 CFR 204.2(c)(2)(vi); 8 CFR 216.5(e)(3)(i). See also U visa regulations 72 Fed. Reg. No. 179, 53014,
53015, 53016, 53018 (September 17, 2007). 22 CFR 214.14(a)(8) and (b)(1).
liii
The word “degradation” here categorizes an instance of battery where the perpetrator held down a spouse while sexually assaulting her to urinate on
her. See Morris v. Stonewall, 1999 Ohio App. LEXIS 5356 (1999). See also Ireland v. United Kingdom, 25 Eur. Ct. H.R. (ser. A) (1975) (stating,
European Convention on Human Rights protects against “moral suffering and degrading treatment that creates a sense of fear, anxiety, and
inferiority in order to humiliate, degrade, and break the victim’s resistance.”
liv
According to Goodman and Dutton’s Coercive Control Model, a credible threat is a form of coercive control. At the center of coercive relationships,
the target believes that negative consequences can and will occur if the target does not comply with the perpetrator’s demands. Thus, a credible
threat in that context, means the perpetrator is communicating to the target that they are able, willing, and ready to carry out a threat for
noncompliance. Mary Ann Dutton and Lisa A. Goodman, Coercion in Intimate Partner Violence: Toward a New Conceptualization, 52,
Sex Roles, 743,
745, 750 (2005), available at https://niwaplibrary.wcl.american.edu/pubs/dutton-goodman-coercive-control-model.
lv
U.S. jurisdictions that specifically list “stalking” as a basis for a domestic violence protection order: (AL, AK, AZ, CA, CO, CT, FL, GA, IN (Ind. Code
Ann. § 34-26-5-2 specifically lists stalking), KY, LA, ME, MD, MI, MS, MO, MT, NV, NJ, NM, NY, NC, OH, RI, SD, TN, USVI, UT, VT, VA,
WA, WV, WI. Jurisdictions with specific stalking protection order statutes or with anti-harassment statutes that explicitly list stalking as grounds for
issuance of a protection order: AK, AZ (harassment under A.R.S. § 12-1809), CA (civil harassment orders for those who suffer harassment or
stalking; workplace violence protection orders includes protections against certain “course of conduct” under Cal.C.C.P. § 527.6), CO, CT, DC,
FL, GA, HI (protection from harassment under HRS § 604-10.5), ID, IL, KS, KY, LA, ME, MA, MI, MN, NE, NV, NH, NJ (stalking restraining
order under N.J. State. Ann. §§ 2C:12-10.1, 2C:12-10.2), NM (county specific court rules allow for harassment restraining orders according to
https://www.womenslaw.org/laws/nm/restraining-orders/civil-restraining-orders-harassment-or-other-harm/county-specific-1
), ND (disorderly
conduct restraining where disorderly conduct means “intrusive or unwanted acts, words, or gestures that are intended to adversely affect the safety,
security, or privacy of another person. For the purposes of this section, disorderly conduct includes human trafficking or attempted human
trafficking as defined in this title” under N.D. Cent. Code Ann. § 12.1-31.2-01), OR, PA, PR, SC, SD, TX, USVI, UT, VT, WA, WV, WI, WY).
Jurisdictions that list behaviors that include stalking tactics as grounds for domestic violence or harassment protection orders: DE, IL, NE, ND, PA
(“Knowingly engaging in a course of conduct or repeatedly committing acts toward another person, including following the person, without proper
authority, under circumstances which place the person in reasonable fear of bodily injury” under 23 Pa. Stat. and Cons. Stat. Ann. § 6102).
Jurisdictions with workplace violence protection orders that include harassment/stalking as basis: AZ (workplace harassment under A.R.S. § 12-
1810), AR (protection against workplace violence and specifically lists harassment and/or stalking as a basis for granting this order under A.C.A. § 11-
5-115), CA (workplace violence protection orders includes protections against certain “course of conduct” under Cal.C.C.P. § 527.8), RI
(workplace violence protection order based on stalking/harassment under RI Gen. Laws § 28-52-2), TN (workplace violence protection order based
on stalking, threats, harassment under TN ST § 20-14-102). See
https://www.womenslaw.org/laws/general/restraining-orders for additional
information about these protection order statutes including many statutory citations.
lvi
Kivisto, A. J., & Porter, M. (2020). Firearm Use Increases Risk of Multiple Victims in Domestic Homicides. Journal of the American Academy of
Psychiatry and the Law, 48(1), 26-34; Smith, S. G., Fowler, K. A., & Niolon, P. H. (2014). Intimate partner homicide and corollary victims in 16
states: National Violent Death Reporting System, 2003-2009. American Journal of Public Health (1971), 104(3), 461-466; Spencer, C. M., & Stith,
S. M. (2020). Risk Factors for Male Perpetration and Female Victimization of Intimate Partner Homicide: A Meta-Analysis. Trauma Violence
Abuse, 21(3), 527-540.
lvii
Some examples are sleep deprivation, restricting what spouse eats, social isolation. For more information, see: Dutton, M.A., Molina, R., & Young, L.
(2015, July 30). Evidence of Coercive Control: Proof of Extreme Cruelty in Immigration Cases and Power and Control Dynamics in Family Law
Cases [PowerPoint slides]. National Immigrant Women’s Advocacy Project, American University, Washington College of Law.
https://niwaplibrary.wcl.american.edu/pubs/powerpoint-evidence-of-coercive-control-extreme-cruelty
.

1
This b
ench card is designed for use in conjunction with the more comprehensive
Judicial Officer Guide for Responding to
Stalking and as a reference when considering the role of stalking in Federal courts; Tribal courts; immigration courts; state
family, juvenile, civil, and criminal court cases; and administrative law adjudications including immigration and Equal
Employment Opportunity Commission adjudications. Judicial officers are strongly encouraged to read
the full Guide prior to
using this bench card during proceedings.
This bench card serves as a reference for judicial officers on stalking behaviors and how these behaviors relate to other crimes,
to be better able to identify stalking in any type of case. Judicial officers are encouraged to make specific findings of fact
regarding stalking and issue detailed orders designed to stop stalking behaviors, hold offenders accountable, and prevent
dangerous consequences.
CONSIDERING/IDENTIFYING STALKING
Stalking can appear in any type of case and it is particularly important to look for indicators when the parties
know one another and/or there is evidence of ongoing harmful contact. Stalking can occur in the context of
other crimes and other crimes can occur in the context of stalking.
Stalking should be considered in protection order and domestic violence hearings
because intimate partner
stalkers are more likely (than stalkers with other relationships to their victims) to physically approach the
victim; be interfering, insulting, and threatening; use weapons; escalate behaviors quickly; and re-offend.
Technology-facilitated stalking (cyber-stalking) needs particular consideration and concern in stalking cases.
Perpetrators of stalking use and misuse technology to facilitate their stalking. They use computers, social
media, mobile phones, and other devices in their stalking behaviors to monitor, contact, control, and isolate
their victims, as well as to damage their victims’ credibility or reputation. The impact of technology-facilitated
stalking is vast and may be just as threatening and fear-inducing as in-person stalking. Victims of technology-
facilitated stalking often report higher levels of fear than individuals who experience in-person stalking
i
ASSESSING STALKING
It is extremely important to note that victims of stalking often do not identify their victimization as stalking or harassment and
are unlikely to use those words to describe what they’re experiencing; instead, they often describe the stalking behaviors and
impacts.
ii
As such, it is important to use a framework for assessing the presence of stalking rather than rely on victims to
identify and name it. Stalkers often try to argue that their behavior is based on a legitimate purpose (to see the kids, to share
the car, to drive down the street, etc.), is a coincidence, or is not itself criminal behavior; however, if their behavior is a pattern
that shows the intent to survey, invade, intimidate, or interfere with/sabotage the victim using the behavior, then their actions
legally meet the evidence-based definition of stalking. Stalking can be done in-person, using technology, or both.
Appendix A

2
SLII STALKING TACTICS
Dr. TK Logan's multi-dimensional framework, focused on Surveillance, Life Invasion, Intimidation, and Interference through
sabotage or attack (SLII) tactics, provides a research-informed approach to assessing stalking behaviors in judicial
proceedings.
iii
The examples of SLII tactics below pertain to all types of victim-stalker relationships.
Follow, watch, monitor, wait for, show up uninvited, track using
software or devices, gather information, proxy stalking (using a
third party to stalk and report on the victim)
Unwanted/nonconsensual contact and communication,
show up without warning, property invasion, public
humiliation, harass friends/family
Explicit and implicit threats, property damage, symbolic
violence, forced confrontations, threat to or actually harm self,
threat to harm others, deportation threats
Financial and/or work sabotage, ruin reputation, custody
interference, keep victim from leaving, road rage, attack
friends/family/children/pets, physical or sexual attack
DURATION, INTENSITY, FREQUENCY
The framework also explains that stalkers use SLII tactics in a dynamic way that can be measured by the Duration, Intensity, and
Frequency of implementation.
•
Duration
is how long the tactics have gone on — when the stalking started and how long it has lasted.
•
Intensity
is the number of different tactics and locations that the stalker employs.
•
Frequency
is how often the stalker makes their presence known — how often the stalker approaches, confronts, and/or
interferes in the victim’s life.
Whether the offender exhibits one continuous tactic or a variety of tactics, the longer the duration and greater the intensity
and frequency of any stalking tactics, the greater the risk of harm, persistence, escalation, and life sabotage
.
iv
Data show
greater victim psychological distress in response to greater frequency of stalking and to any changes in stalker behavior, and
escalation is known to lead to greater violence.
v
ESTABLISHING FEAR
In the vast majority of stalking situations, the stalker knows
their victim
vi
and so may have unique and intimate
knowledge about their victim’s vulnerabilities and what
would scare them. Stalking behaviors often include a
specific meaning only understood by the victim, and may
be intended to seem benign to anyone other than the
victim. When the offender targets a victim with specific
incidents or tactics that the victim finds frightening, this
may show the offender’s intent to frighten them.
Victims react to stalkers in a variety of ways, and fear is
often masked by other emotions: anger, frustration,
hopelessness, despair, or apathy. Some may minimize and
dismiss their stalking as “no big deal.”
3%
6%
20%
9%
44%
32%
4%
9%
19%
8%
41%
43%
Person of Authority
Family Member
Stranger
Brief Encounter
Acquaintance
Current/Former
Intimate Partner
Stalking Victim & Offender Relationships
vi
Female Victims
Male Victims

3
It is helpful to consider how victims change their behaviors to cope with the stalking. At a minimum, these are signs that the
stalker’s behaviors are unwanted and the victim is resisting the contact. Evidence and corroboration of the victim’s fear and
resistance can be found by considering changes and accommodations the victim has made to their life.
So
me victims continue to have contact and engage with the stalker as a safety strategy, to gather information, assess the
offender’s state of mind, and negotiate their safety. Contact on the part of the victim does not mean that the victim is not in
fear or that the stalker’s behaviors are wanted. In fact, it may indicate that the victim is very afraid of the offender and is
contacting the offender to be able to assess and plan the steps they will take to increase safety for themselves and others.
RISK FACTORS
When reviewing a stalking case, there are 14 factors to consider in assessing the risk posed to victims. Evidence-based research
has found that the presence of or increase in any of the factors contributes to increased risk of current and future harm to the
stalking victim.
vii
(Note that there may be additional risk factors unique to a case that do not fit neatly into one of these
categories but that should still be considered.)
Th
e Stalking and Harassment Assessment and Risk Profile (SHARP) is a web-based tool that provides a situational risk profile
(available at www.CoerciveControl.org
). This risk assessment is useful for several considerations: pretrial detention and bail
conditions, which cases may demand greater attention, and sentencing and post-sentencing (e.g., probation or parole).
COURT ORDERS AND FINDINGS
• Courts can specifically design court orders containing no-contact provisions, mitigating direct contact between the
victim and offender, and utilizing other available safety measures. Providing qualified interpreters in proceedings involving
stalking and translating court orders when the offender and/or the victim are limited English proficient promotes offender
compliance and victim safety.
• Identifying and distinguishing stalking from other forms of intimate partner violence occurring in a case enhances the
effectiveness of court orders in protection order and domestic violence related custody and divorce cases. Victims cannot
violate their own protection orders because the orders circumscribe only the offender’s behavior, not the victim’s.
• Detailed findings regarding the stalking behaviors and their frequency, duration, and intensity also help appraise future
judicial officers who hear actions involving the same parties of the severity of the abuse occurring in the case.

4
PROTECTION ORDERS & BAIL CONDITIONS
Consider orally informing the offender of conditions and prohibitions for protection orders and bail in court (particularly the
prohibition from possessing firearms, ammunition, and related permits and their associated verifiable surrender), as well as that
violations can result in revocations of bail, probation, etc. and may be the basis for (additional) criminal charges. Use qualified
interpreters in any criminal, family, or civil case involving people with limited English proficiency. Having court orders translated
into the languages spoken by the offender and/or victim promotes greater compliance and victim safety.
When stalking behaviors are present, both protection orders and bail conditions should:
Include no-contact provisions that carefully specify prohibitions on indirect as well as direct contact, including
contact through the use of technology and social media, and any other conditions (e.g., GPS monitoring or
restrictions on use of digital devices) that will help to ensure the victim’s safety.
Specify that “no contact” includes indirect contact and contact through third parties, as well as social media
posts about, or directed toward, the victim.
Prohibit contact with members of the victim’s family or household and, in appropriate cases, the victim’s
employer and named friends of the victim.
Prohibit the offender from monitoring, tracking, or surveilling the victim, by use of technology or otherwise.
List any locations frequented by the victim and specify the distance that the stalking perpetrator must stay away from
these locations.
Address when the offender and victim regularly frequent the same places (e.g., a church or a gym) — the order should
bar the offender from those locations completely except during times specified in the court order (designing the order
so that the victim is safe to be at the location except during the hours that the offender is authorized to be there).
Specify that if the offender arrives at a public location and the victim is present, the offender must promptly depart.
Prohibit the offender from possessing firearms, ammunition, and firearms permits; require verifiable surrender of
any of these that the offender currently possesses, and orally inform the offender of this prohibition in court.
Require the Prosecuting Attorney in a criminal case be informed of any attempt made by the Defendant to
purchase a weapon that is rejected by a Federal database.
Require electronic monitoring of the offender (e.g., ankle bracelet) and regular in-person reporting to probation.
Pr
ohibit the use of alcohol or recreational drugs.
EXAMPLE OF STALKING FINDINGS
Petitioner, name, is a victim of stalking. Respondent, name, has utilized [insert stalking tactics categories, i.e., Surveillance, Life
Invasion, Intimidation, Interference through sabotage or attack] through the following behaviors [list the behaviors that fall
under the respective category]. These behaviors are found to be stalking tactics. Respondent, name, has executed these
behaviors that display a pattern of stalking [name the pattern; include frequency, duration, and intensity]. Respondent’s pattern
of behavior escalated and resulted in greater threat and/or violence against Petitioner, name. Respondent’s actions constitute
stalking [insert citation to state law definition]. HAVING MADE THESE FINDINGS… [Insert detailed specific orders to stop
that specific behavior].

5
ENDNOTES
i
Fissel, E. R., & Reyns, B. W. (2020). The Aftermath of Cyberstalking: School, Work, Social, and Health Costs of Victimization. American Journal of Criminal Justice, 45(1),
70-87.
ii
Jordan, C. E., Wilcox, P., & Pritchard, A. J. (2007). Stalking acknowledgement and reporting among college women experiencing intrusive behaviors:
Implications for the emergence of a “classic stalking case”. Journal of Criminal Justice, 35(5), 556-569.
iii
Logan, TK & Walker, R. (2017). Stalking: A Multi-dimensional Framework for Assessment and Safety Planning. Trauma, Violence and Abuse, 18(2), 200-
222.
iv
Id.
v
Id.
vi
Smith, S.G., Basile, K.C., & Kresnow, M. (2022). The National Intimate Partner and Sexual Violence Survey (NISVS): 2016/2017 Report on Stalking.
Atlanta, GA: National Center for Injury Prevention and Control, Centers for Disease Control and Prevention.
vii
Logan, TK & Walker, R. (2017). Stalking: A Multi-dimensional Framework for Assessment and Safety Planning. Trauma, Violence and Abuse, 18(2), 200-
222.
Learn more at StalkingAwareness.org
This project was supported by Grant No. 2017-TA-AX-K074 awarded by the Office on Violence Against Women, U.S. Department of Justice. The
opinions, findings, conclusions, and recommendations expressed in this publication/program/exhibition are those of the author(s) and do not
necessarily reflect the views of the Department of Justice, Office on Violence Against Women.






